- Platform
- Solutions
- Modern NDR
- Resources
- Company
Platform
Modern NDR
Resources
Company
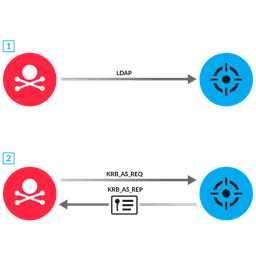
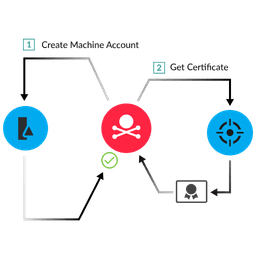
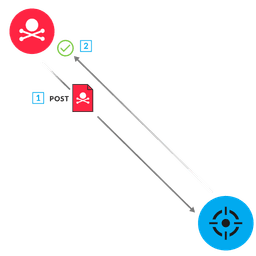
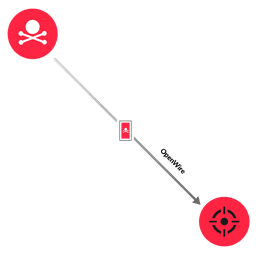
NDR & NPM Detections
Network traffic is the ground truth. ExtraHop unifies NPM and NDR to eliminate blind spots. Our stream processor decodes traffic at line-rate for immediate performance insights, while cloud-scale ML establishes behavioral baselines to detect anomalous threats.
See the truth across hybrid-cloud environments before business disruption.



%2520Proxy-LT.png&w=256&q=75)







Showing 30 of 524 detections