- Platform
- Solutions
- Modern NDR
- Resources
- Company
Platform
Modern NDR
Resources
Company
DETECTION OVERVIEW
Risk Factors
This vulnerability is well known and public exploit code is available. An attacker with LDAP access to a domain controller (DC) and the ability to create a certificate through Active Directory Certificate Services (AD CS) can exploit this vulnerability. A successful exploit creates a privilege escalation path that can grant domain administrator privileges to an attacker.
Category
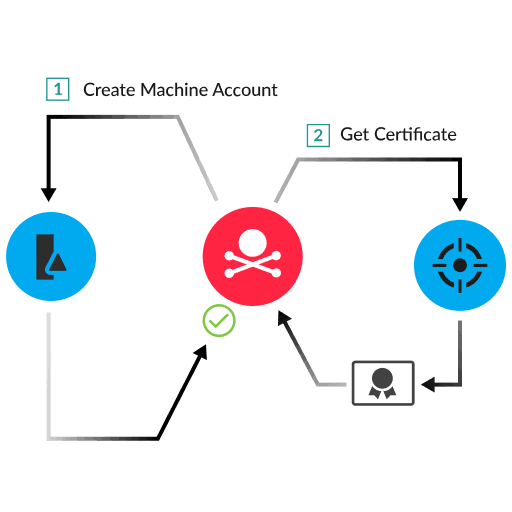
AD Domain Services (AD DS) on a domain controller (DC) allows any domain user to create a machine account with dnsHostName and sAMAccountName properties. These values should be the same. AD DS has a vulnerability that enables an attacker to create or modify a machine account to include different dnsHostName and sAMAccountName properties. AD CS then issues a certificate (essentially a proof of identity) based on the dnsHostName property.
The following diagram shows one scenario for achieving privilege escalation by exploiting this vulnerability. First, the attacker sends a specially designed LDAP request to a DC to create a machine account with a dnsHostName property different from the sAMaccount property. For example, the dnsHostName property might match the dnsHostName of a DC (1). Next, the attacker sends a certificate request to AD CS, which issues a certificate to the attacker that identifies the new account as a DC (2). With this certificate, the attacker can successfully submit Kerberos authentication requests that give the attacker DC privileges.
Network analysis and visibility solutions remain underrepresented in enterprises. Find out why in this preview of a new Wave report.
ExtraHop® Named a Leader in First-Ever Gartner® Magic Quadrant™ for Network Detection and Response
Visit this resource for more information.
This analysis exposes the critical link between an organization's lack of internal visibility and the escalating cost of compromise, demanding an urgent re-evaluation of how core business assets are protected.
Learn why you need to be wary of the claims certain network detection and response providers make about their coverage against the MITRE ATT&CK framework.
Learn how NDR from RevealX helps security teams detect and investigate more adversary TTPs in the MITRE ATT&CK framework than rule-based tools.
