NDR Solution
For Security Operations
Reveal(x) NDR
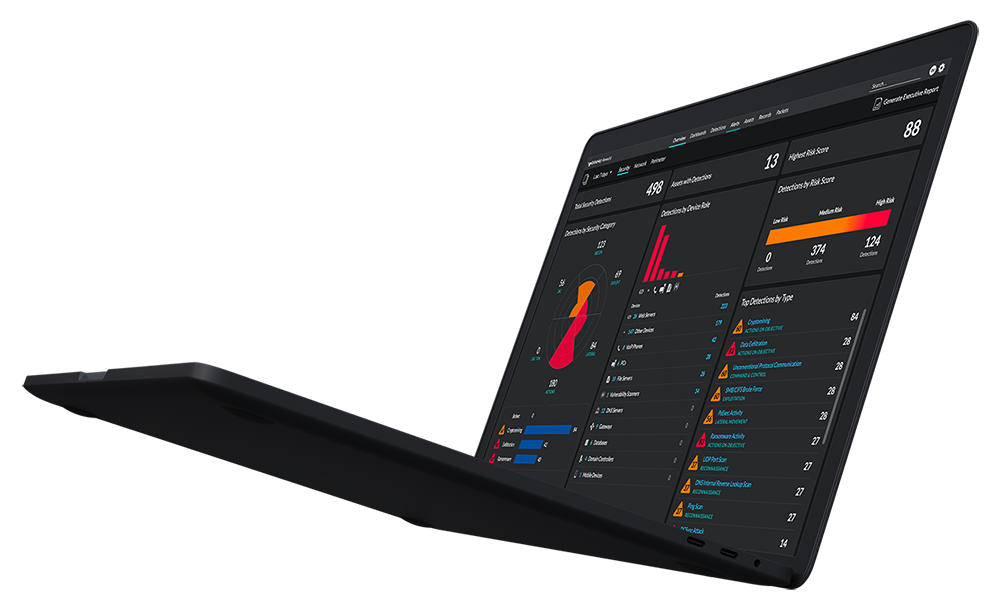
Leverage the network as a central source of truth in order to stop cyberattacks. The ExtraHop Reveal(x) platform allows you to get unparalled visibility and security control across all assets in your organization.
What Exactly Is NDR?
See Definition Here >
See More. Know More.
Stop More Cyberattacks.
COMPLETE VISIBILITY
With a real-time view across the hybrid enterprise, including into sessions encrypted with SSL/TLS cryptography, Reveal(x) makes it easy for analysts, SOC managers, and executives to focus on high priority threats, likely targets, and critical assets.
REAL-TIME DETECTION
By uniting rule- and behavior-based analytics with logical device groups, Reveal(x) detects and triages known and unknown threats with more accuracy and deeper context than log- or agent-based solutions can offer.
INTELLIGENT RESPONSE
Reveal(x) provides full context and one-click investigation workflows for every detection so tier 1 analysts can perform like tier 3 experts—and enables robust automation like agentless device discovery.
Latest Releases

Reveal(x)
Initiatives
Advanced Threats
Protect your business from advanced threats with the leader in NDR
When it comes to advanced threats like supply chain attacks and ransomware, the real battle is not at the edge. Are you ready to beat back adversaries from the inside?
Seamless Cybersecurity
Attackers Can't Evade
While perimeter controls like intrusion detection provide protection and visibility north-south, most enterprises are left blind to insiders, rogues, and low-and-slow attacks. No east-west visibility means that once a host has been compromised, the internal activities are hard to detect, diagnose, or root cause—and thanks to rapidly evolving threats, compromise isn't a question of if but of when.
Modern SOCs meet that challenge by proactively detecting and hunting attackers. They use advanced behavioral analytics and context-rich investigative workflows for effective threat hunting, efficient forensics, and ongoing hygiene to patrol and harden the attack surface. NDR security solutions help SOC teams reclaim the advantage over sophisticated attackers.

Security
Use Cases
Integrations and automations
Extend your security playtform with ExtraHop's Integration Solution Partners

Unparalleled visibility and detection through machine learning. A security must-have.
Read More
Detect Advanced Threats
That Other NDR Tools Miss
Try ExtraHop Reveal(x)
SELF-GUIDED ATTACK SIMULATIONS
Investigate and stop and attack with ExtraHop Reveal(x) as it unfolds in real time.