Enterprise IoT Security
Automatically Identify and Protect IoT Devices
Unmanaged devices leave you exposed at the edge. Get instant, continuous visibility across every device from wherever it connects.

The City of Dallas Security Operations Center (SOC) team monitors all activity for
their security and IT infrastructure.
Service-Layer Discovery & Detection For IoT
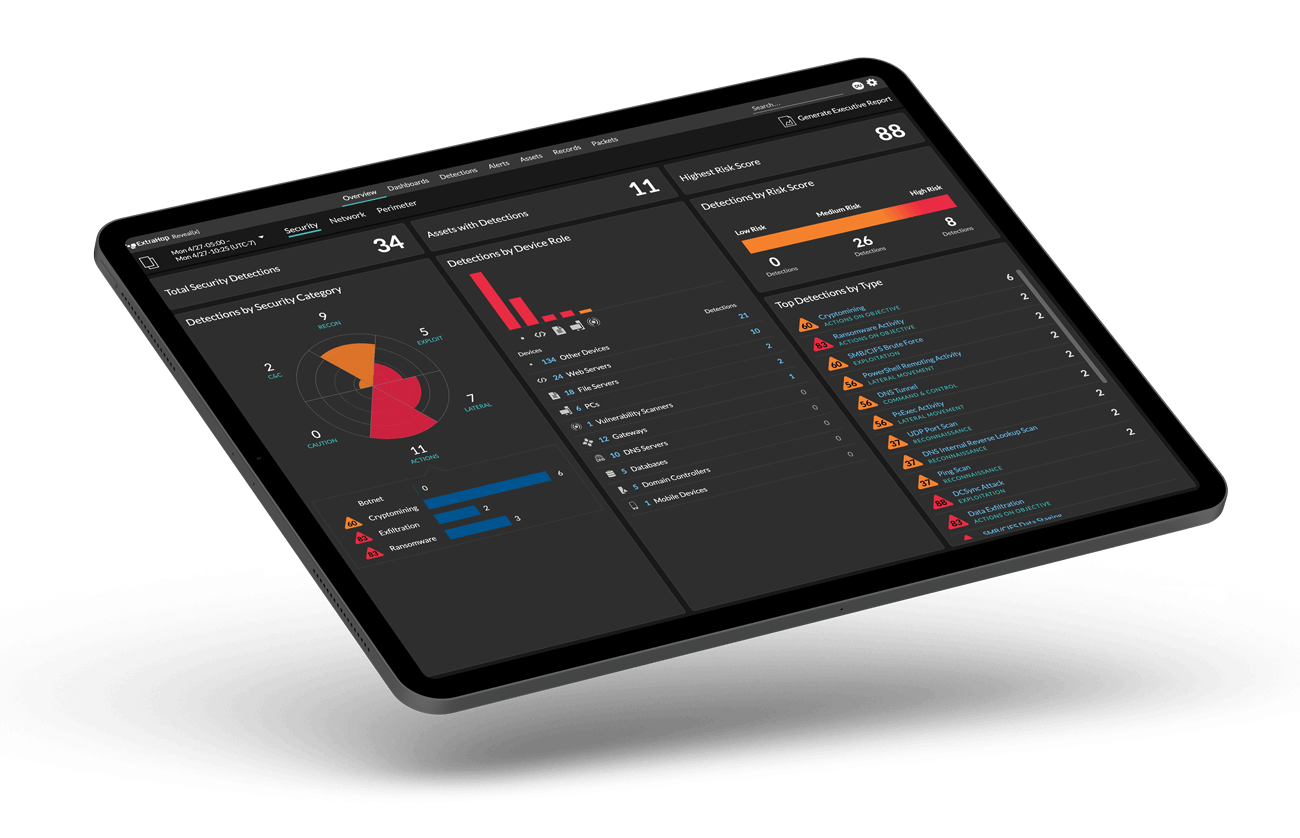
The incredible proliferation of IoT devices has vastly expanded the enterprise attack surface. Discovering, managing, and protecting those devices by traditional means is a labor-intensive nightmare. Applications have become more distributed and the number and variety of connected devices has exploded. Security teams are tasked with the near-impossible: to stop attackers from using these devices as an entry point and as an attack vector for lateral movement, and to do it at scale.
ExtraHop Reveal(x) 360 delivers a passive, scalable enterprise IoT solution you can implement right out of the box for IoT device identification and profiling, service-layer discovery and detection, and threat detection. Our advanced machine learning automatically profiles all devices, infers which services they belong to, and detects violations and threats for quick remediation. Reveal(x) 360 makes it easy for security and IT teams to support and secure the technologies that help their business grow.
eliminate
blind spots
Gain complete visibility across all managed and unmanaged devices, east-west and north-south communications, including encrypted traffic.
83% faster
threat detection
Improve the efficiency of security analysis through investigative workflows with full context that identifies and groups devices and operating systems.
87% faster
threat resolution
Identify anomalous device activity with automated response workflows to stop threats before a breach happens.
Harness the Power of IoT
Without ExtraHop, the investigation [into a new strain of ransomware] would have taken days or weeks, exposing the hospital to potentially catastrophic risk.
Joanne White
CIO,
Wood County Hospital
Start Hunting Right Away
Traditionally, once an adversary gets inside of your perimeter undetected, time is on their side. If no one is watching, they are free to move laterally, live off the land, and mount sophisticated attacks against your organization. This is why even today, dwell time is still measured in months.
Cutting dwell time prevents catastrophic damage by detecting attackers before they reach your most critical assets like domain controllers, intellectual property, and customer databases.
Start hunting in minutes, not months. Reveal(x) 360 integrates with all major cloud vendors' native packet mirroring features in only a few clicks. Nothing to deploy and no agents to load. Adversaries and your lines of business won't even know it is there.
Want to See
For Yourself?
Stop data exfiltration, insider threats, and more
with the full product demo.