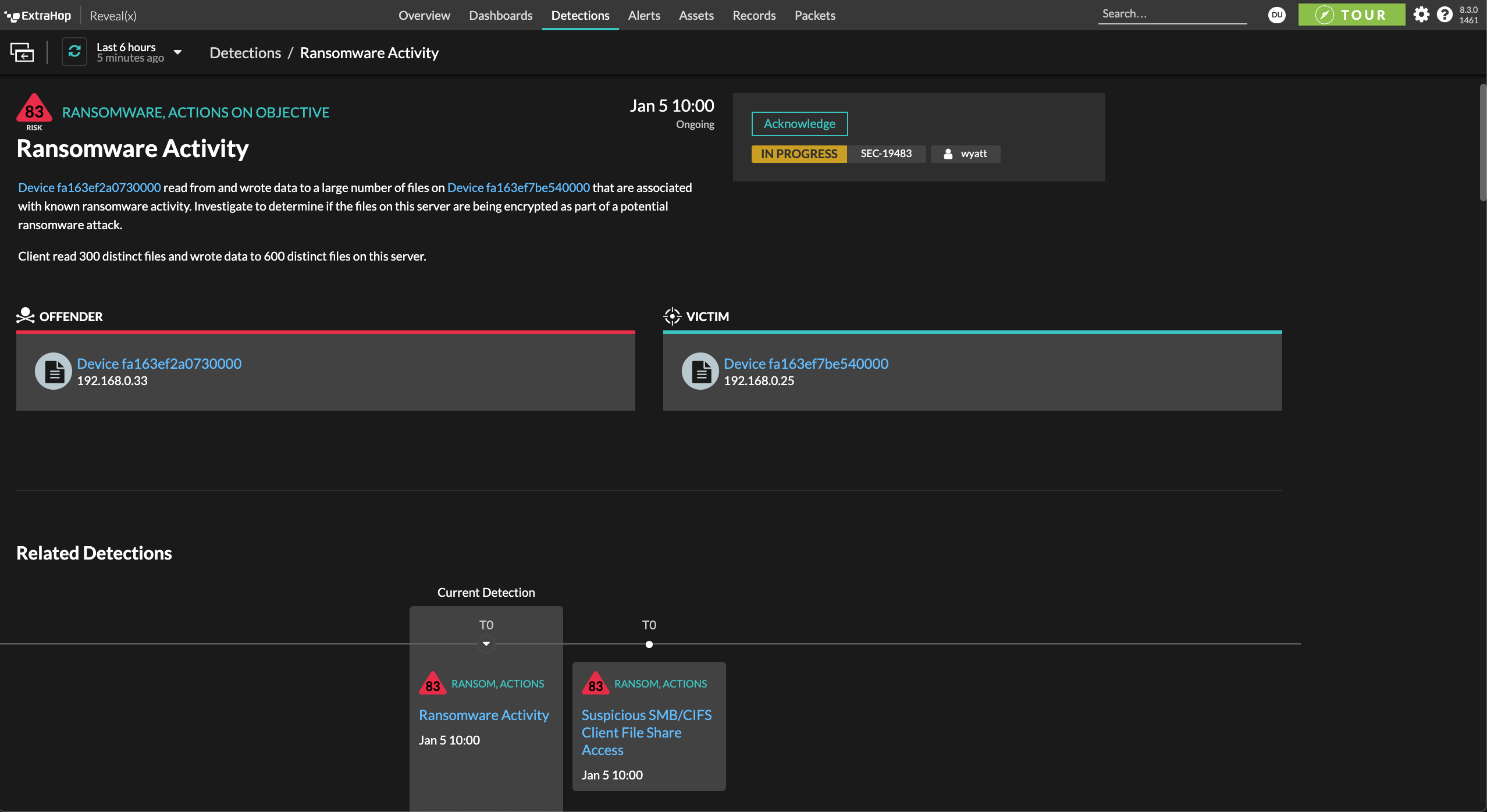
Improve Mean Time to Respond (MTTR)
"Alert spam" contributes to the security analyst's challenge to focus on what really matters.
Sophisticated cyberattacks go undetected for weeks or months, and when discovered, security analysts struggle to contain the compromise and assess its scope. Most detection tools are noisy and generate "ticket spam" to contribute to your security analyst's challenge. Privacy regulations increasingly have strict disclosure requirements that put pressure on incident response teams to conduct their investigations quickly and accurately.
With ExtraHop Reveal(x)
See the Alerts You Care About with Network Context
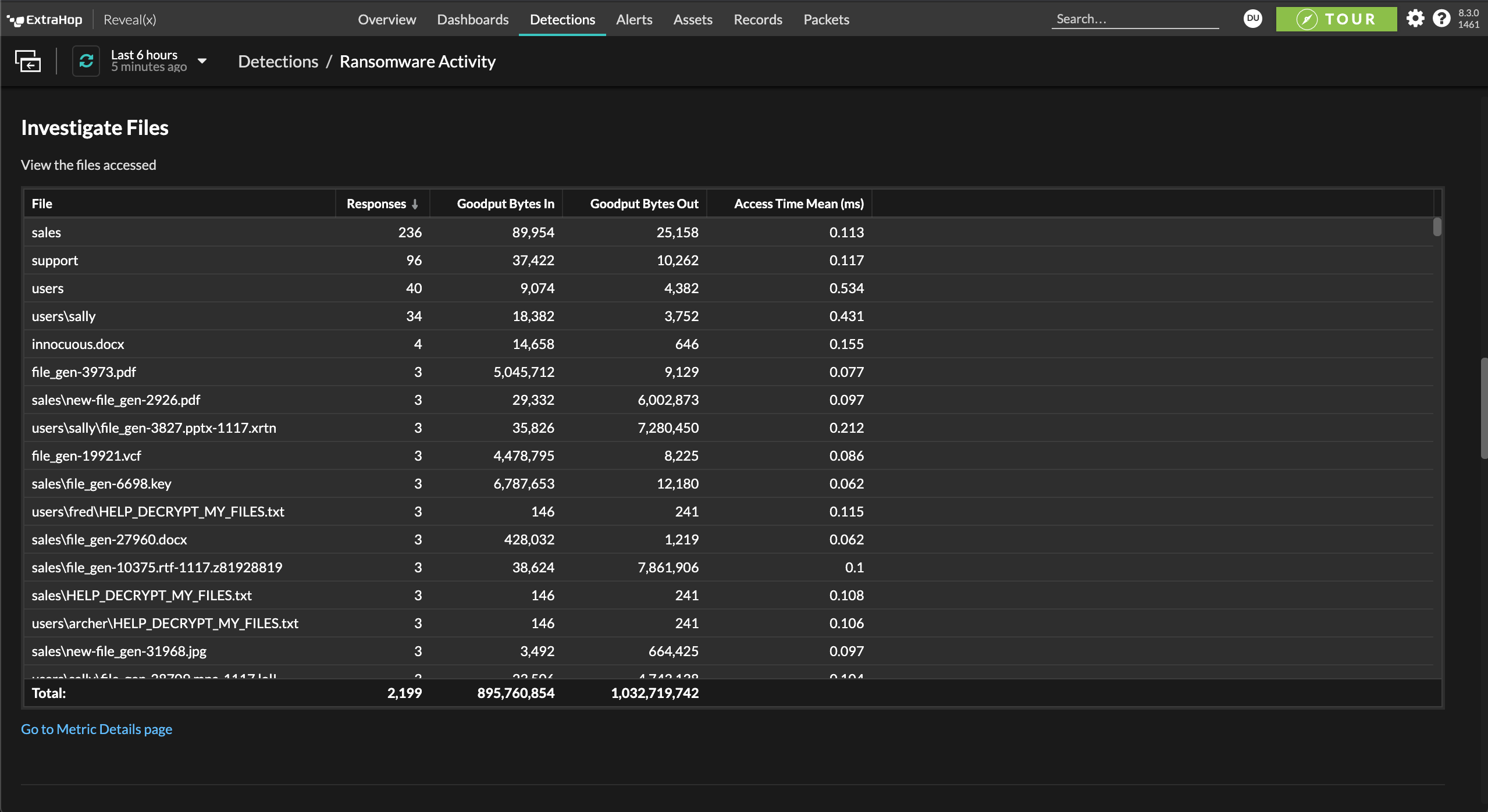
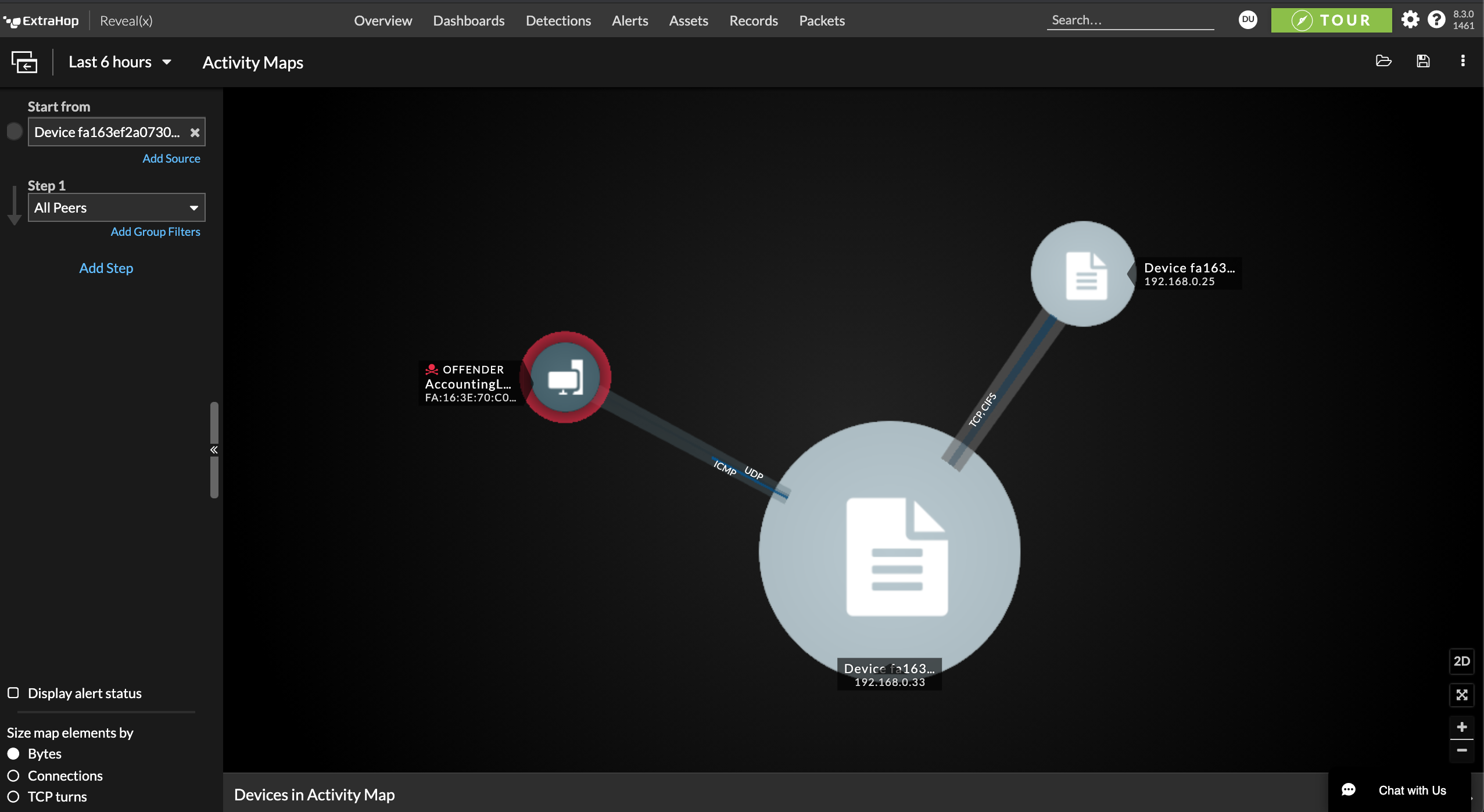
Reveal(x) empowers your analyst to respond quickly and appropriately by including an abundance of contextual information such as a related detection timeline, mapping to MITRE ATT&CK techniques, and compromised critical assets involved. Reveal(x) speeds up the investigation process by enabling analysts to easily trace attack activity and gather artifacts from periods of weeks or months and determine the scope of a potential incident.