Detect Lateral Movement
Once attackers are inside, it is extremely difficult to detect them.
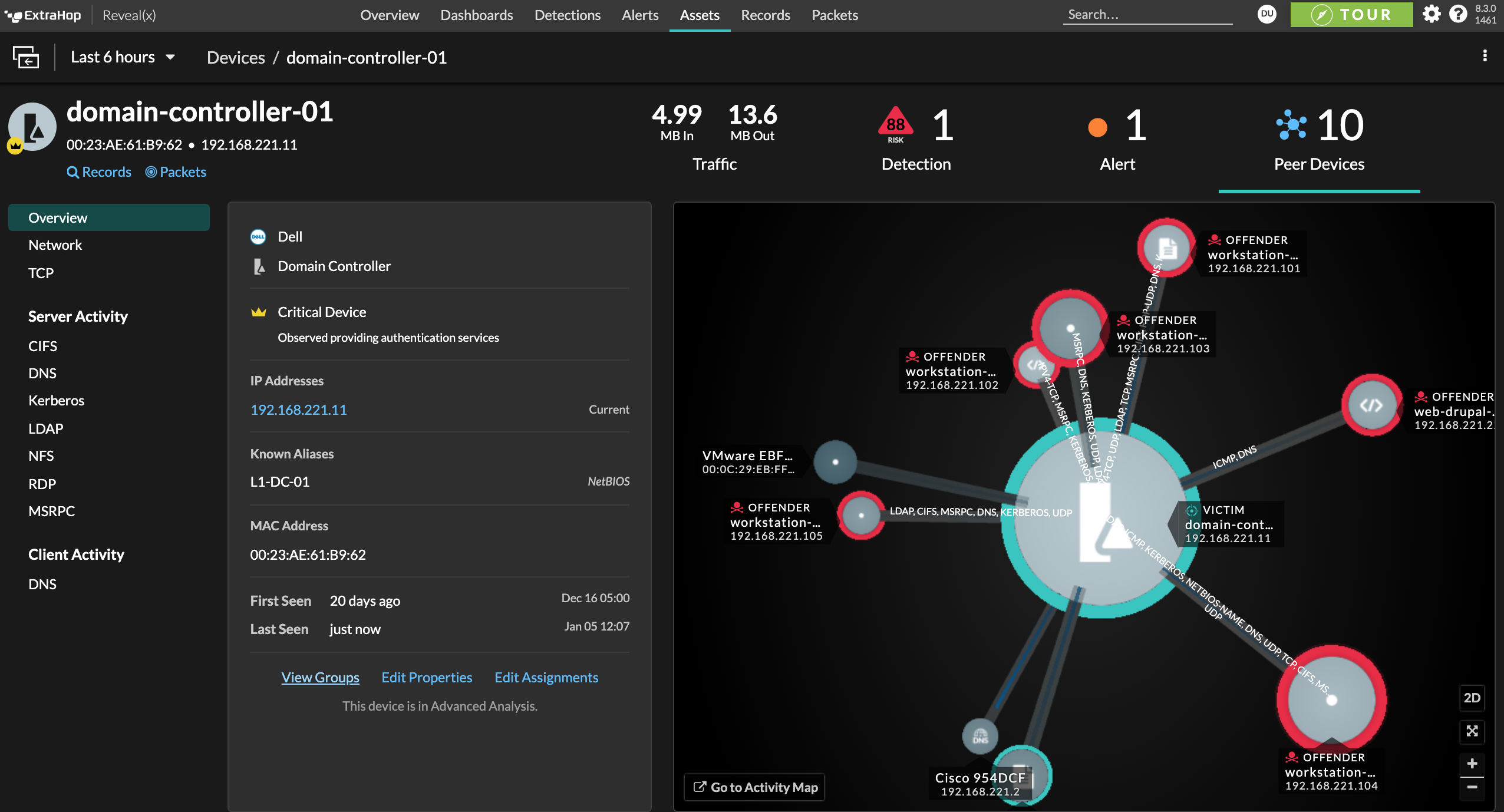
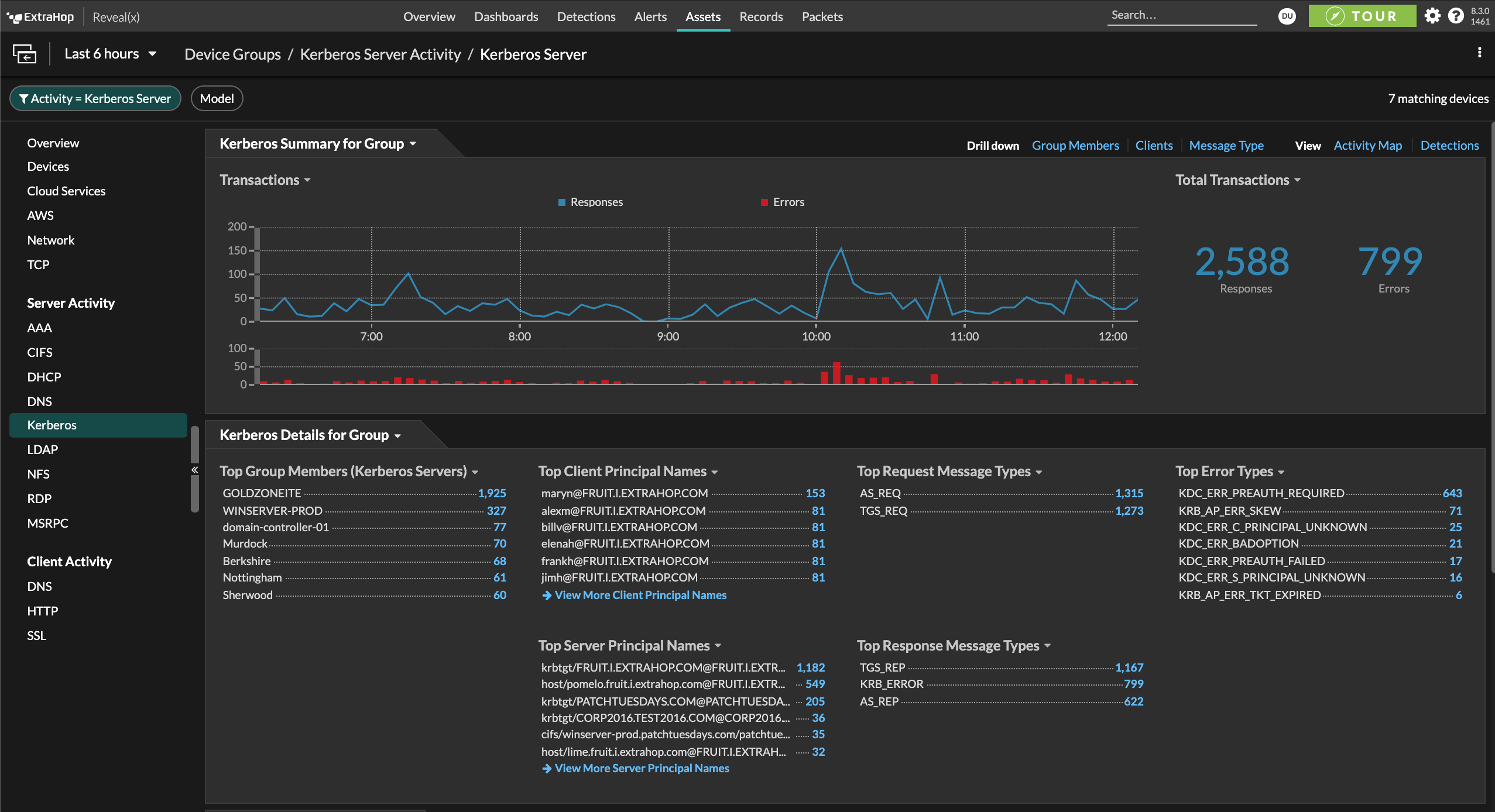
Blind spots in your east-west corridor mean attackers can hide, undetected until they can uncover ways to move laterally throughout your network. Long dwell times provide attackers the time they need to execute a breach.
With ExtraHop Reveal(x)
Detect Lateral Movement to Stop Breaches
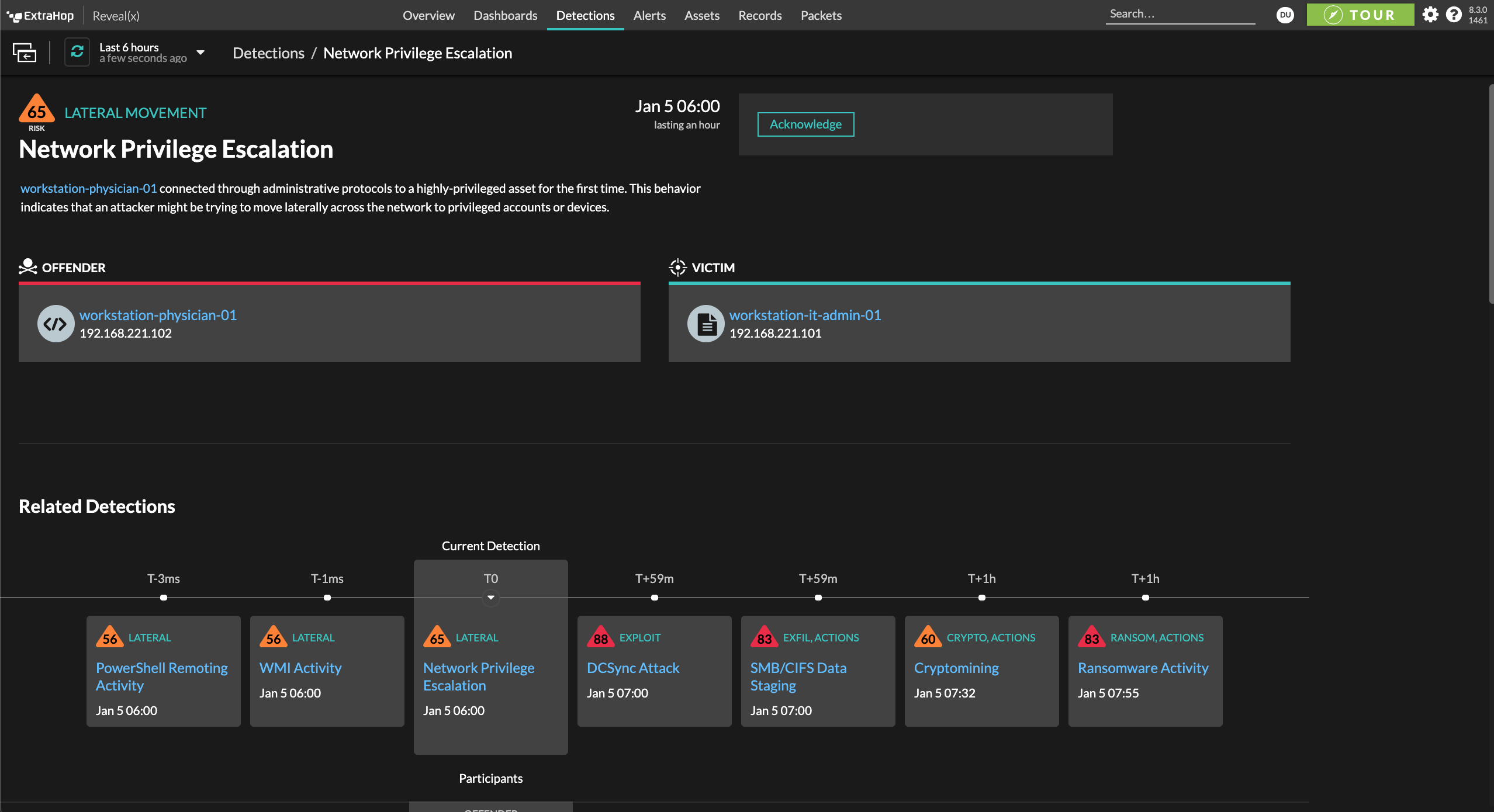
Reveal(x) protects the organization's "crown jewels" from late-stage attacks and probing activities by detecting privilege escalation and lateral movement, and stitches detections together to show the exact sequence of events followed by an attacker, so the security team can stop the breach before it happens.