Challenges
Faster Threat Detection, Investigation, and Remediation
Advanced cyber attackers know how to exploit what you rely on to succeed: access to data, trusted software, and people to get the job done. Once inside, these malicious actors know how to wreak havoc in your network. They move laterally and use encryption to cover their tracks so they can accomplish their real objective, executing ransomware or exfiltrating your valuable customer data and intellectual property. They can cut off access to the critical systems and data you need, all while eroding trust among your customers and your team. Eliminating blind spots and responding to threats in their earliest stages is critical to prevent business disruption and minimize financial impact.
Opportunities
Discover and Classify
RevealX discovers and classifies all devices on the network, then analyzes each transaction. Even SSL/TLS-encrypted traffic is no match for the 80+ enterprise protocols RevealX can decode at up to 100 Gbps. Along with dramatically speeding up detection so you can reduce dwell time of threats in your environment, RevealX provides one-click investigations for each detection.
Identify and Stop Threats Faster
By combining rule-based and behavior-based analytics, ExtraHop RevealX empowers your SOC to identify real threats, faster as well as automate data gathering and correlation for a more efficient investigation workflow. RevealX is the industry leader in Network Detection and Response (NDR), with enterprise-class network traffic analysis that helps you detect malicious behaviors, prioritize investigations into the highest risk threats, and automate the response with leading partners.
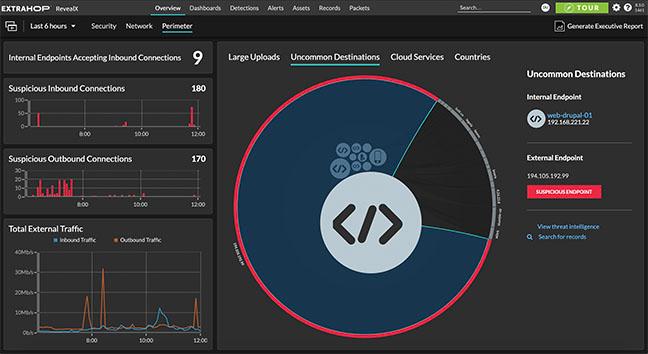
Investigate Smarter
Along with one-click investigations for each detection, RevealX auto-prioritizes your most critical assets so you can easily focus your team's time and energy. Integrations with leading security solutions help security teams respond quickly and confidently to the threats that matter most.
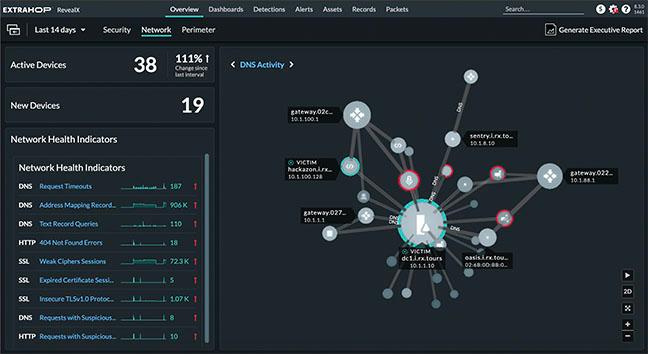
Move at the Speed of Risk
As soon as new vulnerabilities and attack tactics are discovered, our ExtraHop Threat Research team works hard to determine the severity and potential impact for customers. When applicable, they quickly create threat briefings and deploy detectors to RevealX, which starts investigations and searches active network traffic.
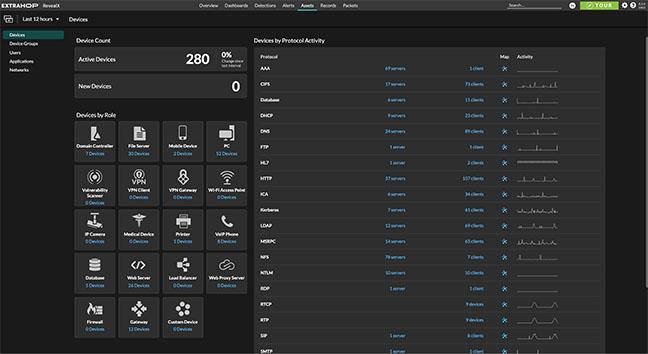
Eradicate Software Supply Chain Attacks with RevealX
The vulnerabilities of your software supply chain are hard to identify because you can rarely access your suppliers’ code. Zero day and unpatched vulnerabilities are leaving gaping holes in your security posture. By monitoring your network traffic, RevealX can detect when an attacker has penetrated your network through your software supply chain and catch attackers before they do any significant damage.

See it in action
RevealX Detects Intruder Actions Across the MITRE ATT&CK Framework

Solution
Market-Leading Network Detection and Response
Leverage the network as a central source of truth in order to stop cyberattacks. The ExtraHop RevealX platform allows you to get unparalleled visibility and security control across all assets in your organization.
Security
Network Detection & Response (NDR)
RevealX NDR
Use the power of network visibility and AI for real-time detection, rapid investigation, and intelligent response for any threat.
Product overview






