- Platform
- Solutions
- Modern NDR
- Resources
- Company
Platform
Modern NDR
Resources
Company
Opportunities
Connecting network activity to the users behind it is essential for faster, more accurate investigations and for stopping the use of compromised credentials and tokens before data theft occurs. Our identity capabilities are built with the SOC analyst in mind—analysts who need fast answers and clear context to keep investigations moving. Most attacks today target people and their access and privileges, not just infrastructure, so it’s critical to understand who is behind the activity, not just what happened. ExtraHop RevealX is designed to bring identity context directly into every step of your investigation workflows, providing you with a clear, real-time picture of account activity across your network without relying solely on endpoint agents. Users are visible, searchable, and fully traceable across the entire platform. By weaving identity data directly into the core experience, we’re making it simple to follow the trail and see all the compromised activity and devices associated with a user, and pivot with confidence into network records and packets, to close the loop and get to the root cause.
SECURITY USE CASE
Challenges
With the move to hybrid networks, remote work, and increased SaaS adoption, the security landscape has fundamentally shifted. As a result, identity has emerged as the main point of access and, consequently, the primary target for adversaries.
Identity is no longer solely an IT concern. Security teams need to understand not just what is happening on the network, but who is involved. Without a clear identity context, investigations can stall, and critical insights can be missed.
81% of breaches involve compromised identities.*
*Verizon 2024 Data Breach Investigations Report (DBIR)
See It in Action
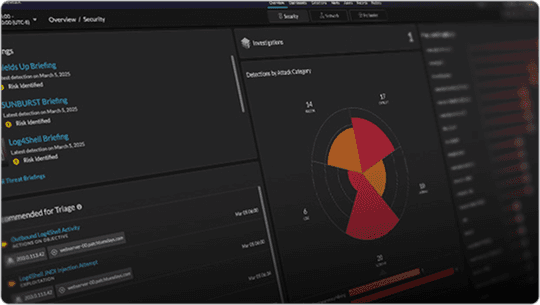
ExtraHop's identity investigation capabilities provide broad user visibility, efficient filtering, deep dives into devices and network records, and seamless pivoting to security detections, for optimized threat response.
Solution
Leverage the network as a source of truth in order to stop cyberattacks. The ExtraHop RevealX platform allows you to get unparalleled visibility and security control across all assets in your organization.
Security
Use the power of network visibility and AI for real-time detection, rapid investigation, and intelligent response for any threat.
