- Platform
- Solutions
- Modern NDR
- Resources
- Company
Platform
Modern NDR
Resources
Company
DETECTION OVERVIEW
Risk Factors
Cobalt Strike is a publicly available and well known tool associated with pen testing, security assessments, and persistent, planned attacks. Outbound connections to Cobalt Strike team servers are associated with command-and-control (C&C) activity. Through a persistent C&C channel, an attacker can remotely control a device and gain an entry point for further attacks on the network.
Category
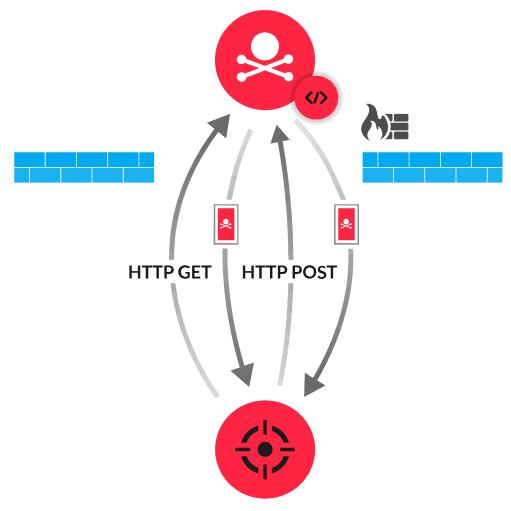
Cobalt Strike is an attack simulation toolkit that is often associated with malicious activity. Attackers install the Cobalt Strike Beacon payload on a compromised device and the beacon initiates a connection to a C&C server, referred to as the Cobalt Strike team server. Messages between compromised devices and Cobalt Strike team servers can include encrypted information such as command output.
Block inbound and outbound traffic from suspicious IP addresses at the network perimeter
Quarantine the device while checking for the presence of malware
Network analysis and visibility solutions remain underrepresented in enterprises. Find out why in this preview of a new Wave report.
ExtraHop® Named a Leader in First-Ever Gartner® Magic Quadrant™ for Network Detection and Response
Visit this resource for more information.
This analysis exposes the critical link between an organization's lack of internal visibility and the escalating cost of compromise, demanding an urgent re-evaluation of how core business assets are protected.
Learn why you need to be wary of the claims certain network detection and response providers make about their coverage against the MITRE ATT&CK framework.
Learn how NDR from RevealX helps security teams detect and investigate more adversary TTPs in the MITRE ATT&CK framework than rule-based tools.
