 Blog
Blog
REvil Ransomware Attack and Supply Chain Risk
Jeff Costlow
July 6, 2021
On July 3, IT management software provider Kaseya disclosed that they were the victim of a sophisticated cyberattack. In response, the company quickly suspended SaaS operations and urged on-premises users to shut down their VSA servers, but not before up to 1,500 organizations in at least 17 countries were affected. Indicators of compromise and a ransom note identified the attackers as the ransomware-as-a-service gang REvil. As of Sunday, REvil was demanding a $70 million cryptocurrency payment in exchange for the decryption keys.
Detect Outbound Requests to Kaseya
Shortly after the Kaseya VSA–based supply chain ransomware attack was disclosed, ExtraHop rolled out a detector that identifies any outbound requests to Kaseya VSA services. As of Tuesday morning, just over 4% of ExtraHop Reveal(x) sensors were still detecting outbound requests to Kaseya servers. ExtraHop recommends that all Kaseya customers immediately terminate connections with Kaseya until the issue is resolved. ExtraHop customers can use the Reveal(x) detector to determine whether they have any remaining connections.
In addition to the detection, ExtraHop also issued an in-product Threat Briefing on the Kaseya VSA-based supply chain ransomware attack to help security and network personnel understand the situation and take action.
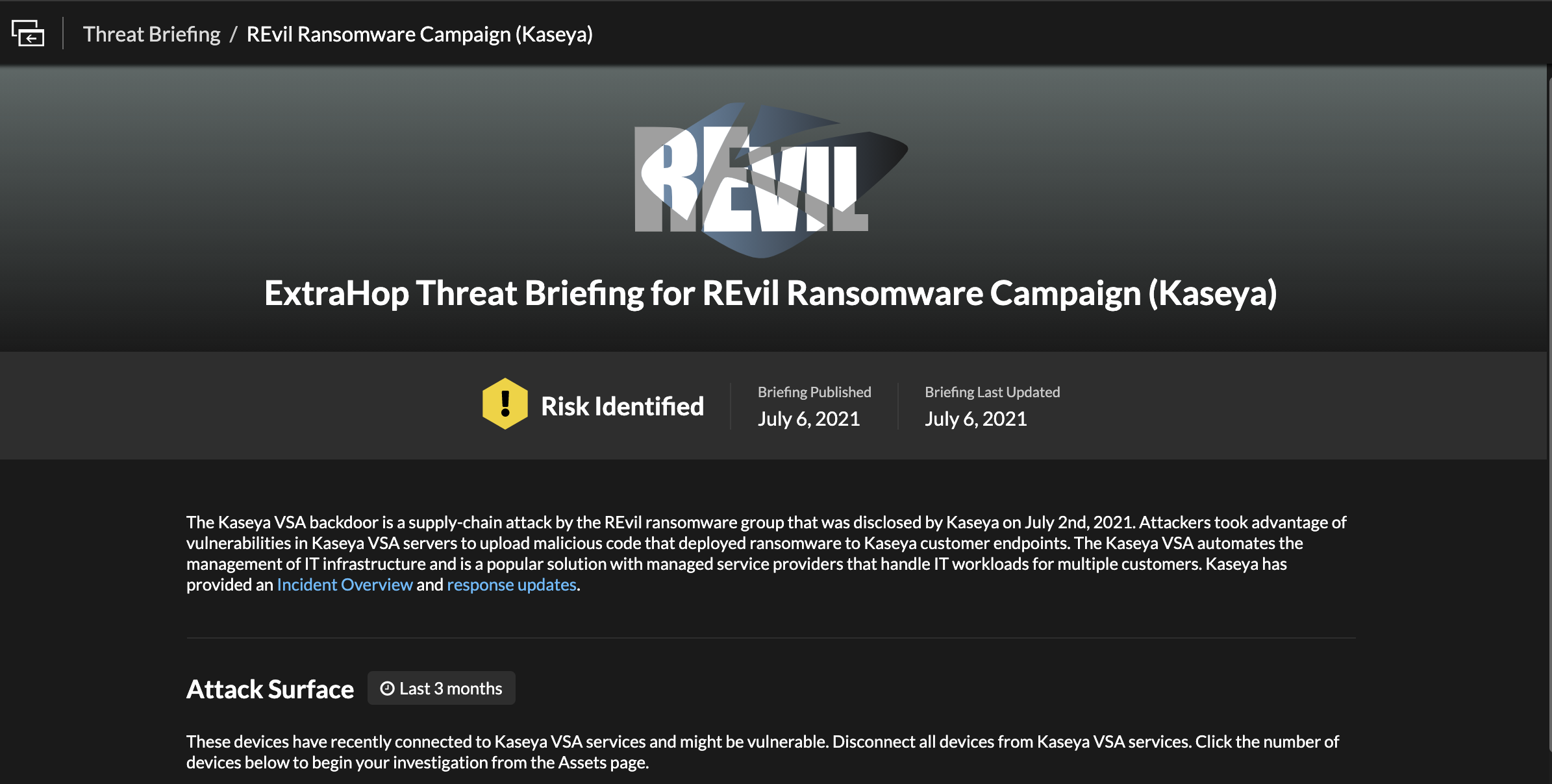
What is the Kaseya VSA Ransomware Attack?
Attackers took advantage of a vulnerability in Kaseya VSA, a remote monitoring and management tool, in order to gain access and spread downstream to Kaseya's customers, impacting up to 1,500 businesses in a supply chain attack. Reports indicate that initial access to Kaseya's infrastructure was achieved using an authentication bypass vulnerability. Once they had access, they were able to use the VSA Server to deploy ransomware on customer devices.
Kaseya and the NotPetya Supply Chain Attack
The Kaseya ransomware attack came almost exactly four years to the day after the NotPetya cyberattack, one of the costliest cyber events in history. Believed to have been perpetrated by Russian nation-state adversaries, NotPetya used a software supply chain compromise to permanently encrypt hundreds of millions of files across organizations around the world. While NotPetya looked like ransomware, it wasn't. There were no decryption keys, because the purpose wasn't to extort a ransom. Instead, it's believed that NotPetya was intended, first and foremost, to be destructive.
The REvil compromise of Kaseya bears many of the same hallmarks as NotPetya. It used a compromise of a widely used software to rapidly spread ransomware on a massive scale. And it shows just how quickly cyber criminal gangs have advanced their techniques.
In the four years since NotPetya, the scope, severity, and sophistication of ransomware has continued to increase dramatically as cyber crime organizations incorporate more and more advanced persistent threat (APT) tactics. It wasn't until 2021 that the full extent of the use of APT tactics in ransomware became apparent. The REvil attack on Acer (until this week, the highest ransom demand in history at $50 million), followed by the DarkSide pipeline attack brought into sharp relief how sophisticated these criminal enterprises have become. According to ExtraHop VP of Security Services Mark Bowling, these attacks should no longer be characterized as "ransomware." Rather, they should now be considered advanced extortionate persistent threats.
Don't Ignore Supply Chain Risk
The Kaseya attack is a painful reminder of a type of risk that is often ignored or underestimated in enterprise security: IT supply chain risk. When third parties connect to your enterprise network for any reason, it exposes you to risk. Organizations that use third-party managed service providers (MSPs) for security are subject to the security policies and risks of those third parties. Many such MSPs use Kaseya, leaving them and all of their customers subject to the security policies and risks that Kaseya itself is exposed to.
In this case, the compromise of Kaseya led to downstream compromises in the form of ransomware, affecting thousands of other organizations. This is the nature of software supply chain attacks which are growing ever more common—no doubt encouraged by the effectiveness of previous attacks.
It is impossible to run an enterprise without accepting some of this type of risk, but there are things you can do to reduce it.
- Scrutinize the security policies and procedures of any third party you onboard. Understand the risk you are introducing. Asking to see vendor's SOC2 or SOC3 reports, verifications of PCI and HIPAA compliance, and other certifications that validate their security posture.
- Monitor network traffic caused by the third party. This includes traffic coming into your system from theirs and traffic going out from your system to theirs. You probably can't put endpoint agents on their devices or consume their activity logs, but you can always monitor the network traffic they generate to your system.
- Monitor internal network traffic between endpoints inside your environment. This is especially important between devices that are controlled or touched at all by the third party you have allowed access. If that third party, such as Kaseya, becomes compromised, the devices they can access in your environment immediately become potential vectors for ransomware, command & control activity, and data exfiltration.
Supply chain attacks make use of trusted pathways like software auto updates and, in the case of Kaseya, service providers with privileged access. It is no longer safe, if it ever was, to simply trust these connections. You need to verify that their behavior is consistent with the purpose of their connection and that they are not introducing a level of risk you're unwilling to accept.
A network detection and response (NDR) tool such as ExtraHop Reveal(x) 360 can provide the visibility you need to monitor third parties and take back the upper hand from attackers who hope to exploit supply chain vulnerabilities.
Discover more