- Platform
- Solutions
- Modern NDR
- Resources
- Company
Platform
Modern NDR
Resources
Company
DETECTION OVERVIEW
Risk Factors
This vulnerability is well known and multiple PoC exploits are publicly available. An unauthenticated attacker can bypass authentication, achieve remote code execution (RCE), and maintain persistent access to the server, which allows the attacker to launch further attacks on the network.
Category
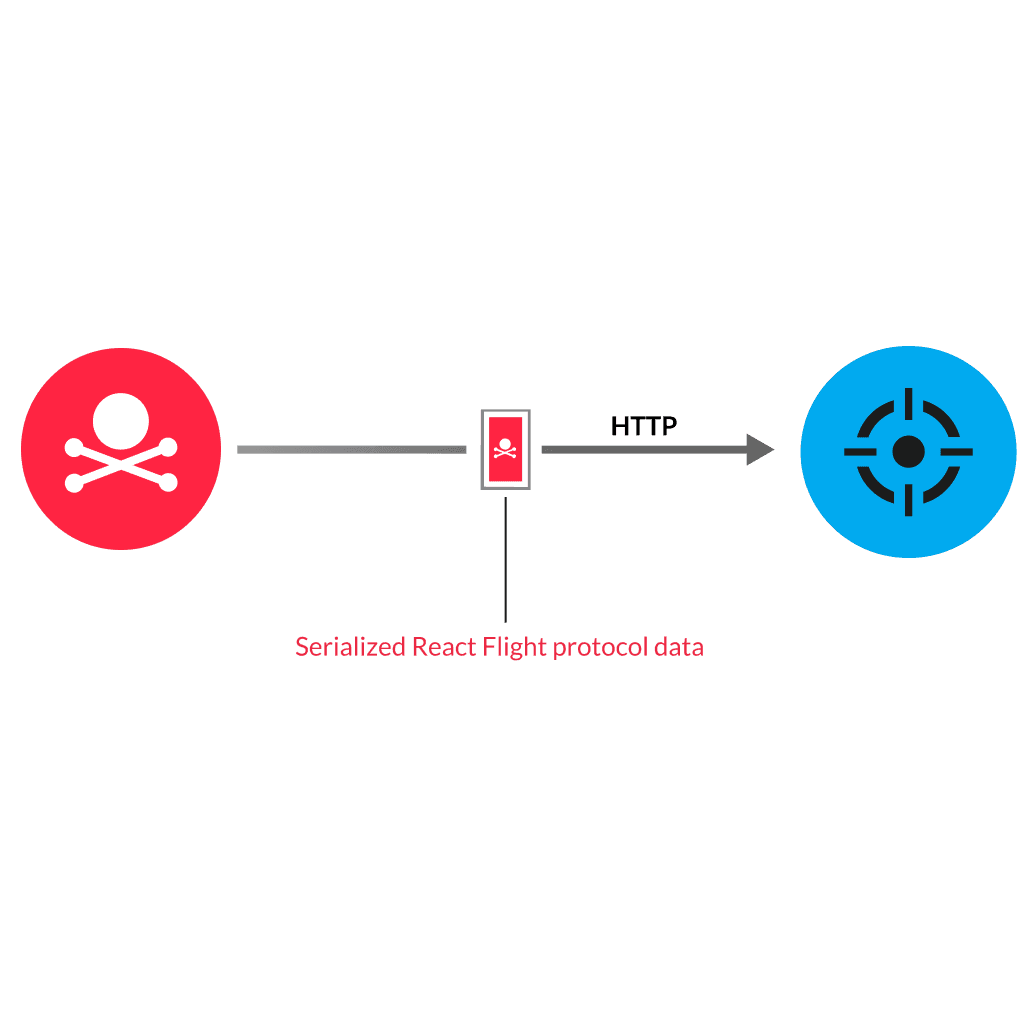
React Server Components, an architectural feature of the React Javascript library, has an unsafe deserialization vulnerability that enables an attacker to inject and run arbitrary JavaScript code.
An attacker sends an HTTP POST request with a specially-crafted, multi-part payload in the request body that includes a serialized object. The React Flight protocol does not validate the serialized data, which enables the server to process user-controlled input. The attacker is then able to run the code to gain full compromise of the server. The HTTP response contains the “Content-Type: text/x-component” header, which confirms that the React Flight protocol deserialized the object and the payload was processed in-memory on the victim device.
Upgrade to React Server Components 19.01, 19.1.2, or 19.2.1
