- Platform
- Solutions
- Modern NDR
- Resources
- Company
Platform
Modern NDR
Resources
Company
DETECTION OVERVIEW
Risk Factors
An unauthorized attacker can exploit an unpatched version of the Oracle WebLogic Server and gain complete control of the server, which provides an entry point for further attacks on your network.
Category
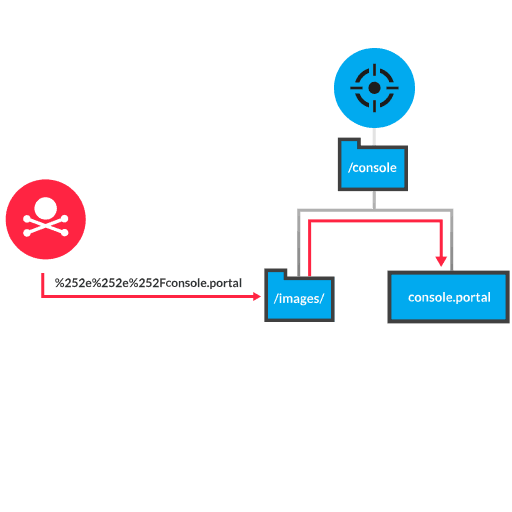
The Console component of Oracle Fusion Middleware is a web-based administration portal for managing an Oracle WebLogic Server. A vulnerability exists in the Console component that processes incoming HTTP requests with malicious parameters. An unauthenticated attacker submits an HTTP request for a static resource or image, where the URI contains a directory traversal fragment (such as ../ or %252E%252E%252F) and the administration portal (console.portal). When the Console processes the request, a malicious payload within the request traverses the directory and arrives at the portal. The WebLogic Server then runs the payload code. Depending on the objective, the payload can help the attacker establish a shell session, install cryptocurrency mining software, or install ransomware.
Apply relevant patches for affected server versions
