- Platform
- Solutions
- Modern NDR
- Resources
- Company
Platform
Modern NDR
Resources
Company
DETECTION OVERVIEW
Risk Factors
An unauthorized attacker can exploit an unpatched version of an Oracle WebLogic application server and run arbitrary commands. An attacker could also gain complete control of a device, providing an entry point for further attacks on your network.
Category
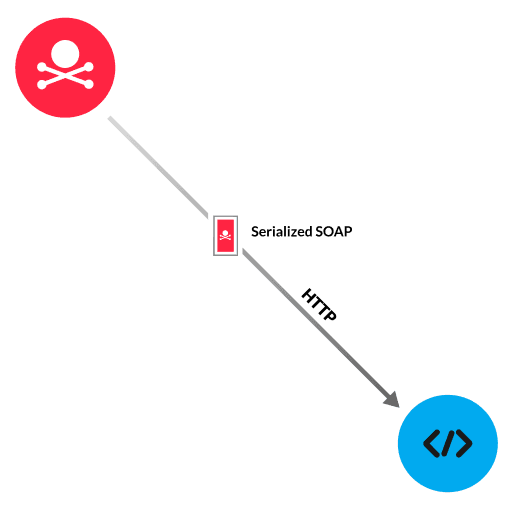
Oracle WebLogic is a Java application server. An attacker with network access or control of a malicious application server can run arbitrary commands remotely through an Oracle WebLogic Server without user credentials. First, the attacker serializes an arbitrary command or malicious payload and embeds it in a SOAP message. Then the attacker encapsulates the SOAP message in an HTTP POST request and sends the request to the WebLogic Server. Depending on the objective, the attacker can establish a shell session, install cryptocurrency mining software, or install ransomware.
