- Platform
- Solutions
- Modern NDR
- Resources
- Company
Platform
Modern NDR
Resources
Company
DETECTION OVERVIEW
Risk Factors
This vulnerability affects any DNS server with Dynamic Zone Updates enabled. However, an attacker needs to infiltrate a network, gain access to authenticated clients with specific configurations, and have the ability to create custom DNS packets. If the exploit is successful, the attacker can cause a denial of service (DoS) or gain control of the DNS server.
Category
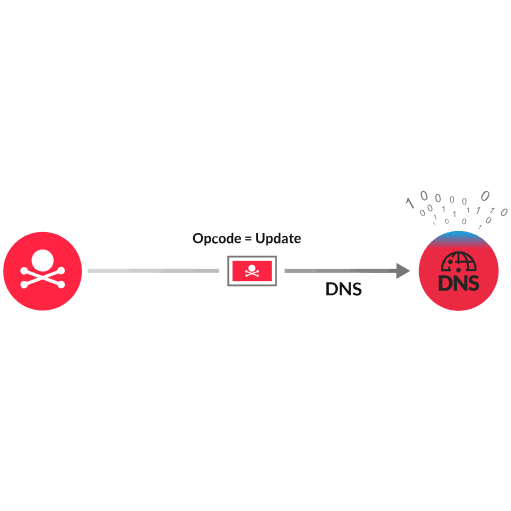
DNS records contain information about a domain, such as an IP address. DNS Zones can be configured on Windows DNS servers (acting as an authoritative nameserver for a domain) to organize records. Typically, a client sends a DNS request that retrieves record information from a DNS server. But a feature called Dynamic Zone Updates enables clients to send a DNS request that updates a record on a DNS server. A vulnerability exists in how the DNS server processes DNS requests for Dynamic Zone Updates. The attacker can send multiple DNS requests that each contain a Signature (SIG) record with a payload of an unexpected size. As the Windows DNS Server processes the requests, a memory allocation error occurs, leading to a heap-based overflow. Malicious, arbitrary code can now run on the Windows DNS Server.
Install relevant patches for affected versions
If unable to patch, limit Dynamic Zone Updates to only accept update requests from trusted servers
Network analysis and visibility solutions remain underrepresented in enterprises. Find out why in this preview of a new Wave report.
ExtraHop® Named a Leader in First-Ever Gartner® Magic Quadrant™ for Network Detection and Response
Visit this resource for more information.
This analysis exposes the critical link between an organization's lack of internal visibility and the escalating cost of compromise, demanding an urgent re-evaluation of how core business assets are protected.
Learn why you need to be wary of the claims certain network detection and response providers make about their coverage against the MITRE ATT&CK framework.
Learn how NDR from RevealX helps security teams detect and investigate more adversary TTPs in the MITRE ATT&CK framework than rule-based tools.
