- Platform
- Solutions
- Modern NDR
- Resources
- Company
Platform
Modern NDR
Resources
Company
DETECTION OVERVIEW
Risk Factors
Well-known attack tools such as Rubeus and Impacket can help an attacker create a diamond ticket. But this attack has many prerequisites, including internal network access and a stolen encryption key. A diamond ticket can allow access to any AD service or resource as any user, helping the attacker achieve attack objectives.
Category
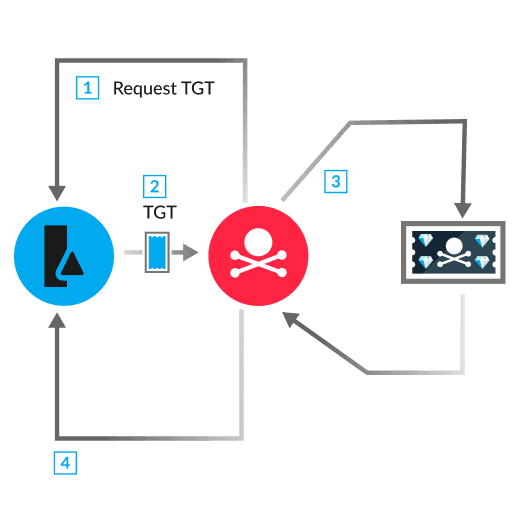
Kerberos is an authentication protocol within Windows Active Directory (AD) environments that creates tickets encrypted with account keys to verify identity and permissions. A ticket contains user, computer, or service account credentials that are encrypted with a cipher algorithm. Every AD domain has a Key Distribution Center (KDC), which consists of two services that are usually installed on a domain controller (DC): the KDC Authentication Server (AS) and the ticket-granting service (TGS). After a user successfully authenticates to the KDC AS, a ticket-granting ticket (TGT) is assigned to the user. The TGT acts as the proof of identity.
When a user wants to access a service, such as a database or printer, the user submits their TGT to the TGS. All verification of Kerberos tickets, including encrypting and decrypting TGTs, is done by the KRBTGT account. The KRBTGT account is a local default Windows account associated with the AS. A malicious, forged TGT is considered a valid ticket if that ticket was encrypted with the KRBTGT account.
If an attacker steals both the KRBTGT account key from a DC in an AES256 format and credentials for a low-privileged AD user, the attacker can perform a Kerberos diamond ticket attack. The first step is to leverage the credentials of a low-privileged user to request a legitimate TGT from the DC (1). Next, the attacker decrypts the TGT with the KRBTGT account key and modifies the TGT with the goal of either impersonating a highly privileged domain user or escalating privileges of the current user (3). To impersonate another user, the attacker modifies the cname, user relative identifier (RID), and group membership RID fields in the Privilege Attribute Certificate (PAC) portion of TGT. To escalate privileges of the current user, the attacker only modifies the group membership RID field. After re-encrypting the modified TGT with the KRBTGT account key, the attacker creates a diamond ticket. The attacker can now submit the diamond ticket in a TGS request (TGS_REQ) to the DC to access other services (4). The DC trusts the diamond ticket because it was encrypted with the KRBTGT account key, and provides a service ticket for the requested service with the name of the low-privileged user or the impersonated user in the response (TGS_REP). Finally, the attacker accesses the service by submitting the service ticket to the system hosting the service.
Reset the built-in KRBTGT account password twice, which will invalidate existing diamond tickets
For each domain, change the KRBTGT account password, force replication, and change the password again
Limit the account permissions of highly privileged users to DCs and specific servers
Delegate administrative functions to separate accounts
Network analysis and visibility solutions remain underrepresented in enterprises. Find out why in this preview of a new Wave report.
ExtraHop® Named a Leader in First-Ever Gartner® Magic Quadrant™ for Network Detection and Response
Visit this resource for more information.
This analysis exposes the critical link between an organization's lack of internal visibility and the escalating cost of compromise, demanding an urgent re-evaluation of how core business assets are protected.
Learn why you need to be wary of the claims certain network detection and response providers make about their coverage against the MITRE ATT&CK framework.
Learn how NDR from RevealX helps security teams detect and investigate more adversary TTPs in the MITRE ATT&CK framework than rule-based tools.
