- Platform
- Solutions
- Modern NDR
- Resources
- Company
Platform
Modern NDR
Resources
Company
DETECTION OVERVIEW
Risk Factors
This vulnerability can affect Windows devices running applications that employ HTTP.sys, such as Internet Information Services (IIS), Windows Remote Management WS-Management (WinRM), or Web Services for Devices (WSD). An attacker can cause a denial of service (DoS) or potentially gain complete control of a device. This exploit is wormable.
Category
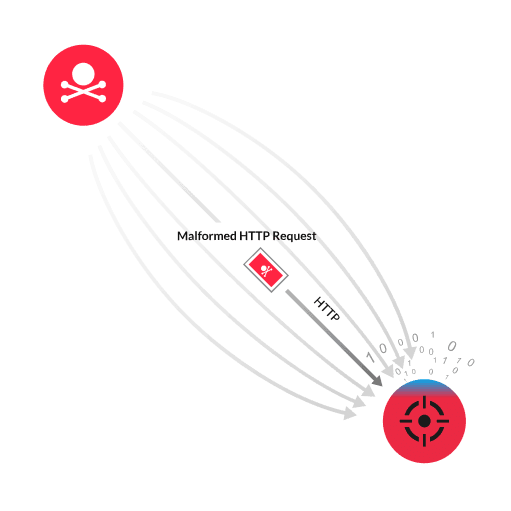
The HTTP Protocol Stack (HTTP.sys) is a kernel-mode device driver in Windows devices responsible for processing inbound HTTP requests and creating outbound HTTP responses. For example, HTTP.sys provides web server functionality to internet-facing applications such as Internet Information Services (IIS), Exchange, and Sharepoint. A vulnerability exists in how HTTP.sys processes incoming HTTP requests. An attacker crafts a sequence of HTTP requests to send to the vulnerable server. The sequence begins with several HTTP GET requests that have large headers. The sequence is completed with a malformed HTTP GET request that is missing an HTTP version token at the end of the request. HTTP.sys incorrectly processes the last malformed request in a way that corrupts a critical data structure in the kernel. The corrupt data structure can cause a denial of service (DoS) and potentially lead to remote command execution (RCE).
Install patches for relevant versions
For Windows Server 2019 and Windows 10 version 1809 that are not vulnerable by default (meaning that HTTP Trailer Support has been enabled), delete the DWORD registry value for EnableTrailerSupport in HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\HTTP\Parameters
Network analysis and visibility solutions remain underrepresented in enterprises. Find out why in this preview of a new Wave report.
ExtraHop® Named a Leader in First-Ever Gartner® Magic Quadrant™ for Network Detection and Response
Visit this resource for more information.
This analysis exposes the critical link between an organization's lack of internal visibility and the escalating cost of compromise, demanding an urgent re-evaluation of how core business assets are protected.
Learn why you need to be wary of the claims certain network detection and response providers make about their coverage against the MITRE ATT&CK framework.
Learn how NDR from RevealX helps security teams detect and investigate more adversary TTPs in the MITRE ATT&CK framework than rule-based tools.
