- Platform
- Solutions
- Modern NDR
- Resources
- Company
Platform
Modern NDR
Resources
Company
DETECTION OVERVIEW
Risk Factors
Windows servers are commonly deployed in enterprise environments, and this well known vulnerability can affect thousands of devices. A remote, unauthenticated attacker can easily exploit this vulnerability with a simple DNS infrastructure. If the exploit is successful, the attacker can gain administrator privileges on targeted servers, seize control of critical assets such as domain controllers, and spread malware across the network with a self-replicating worm.
Category
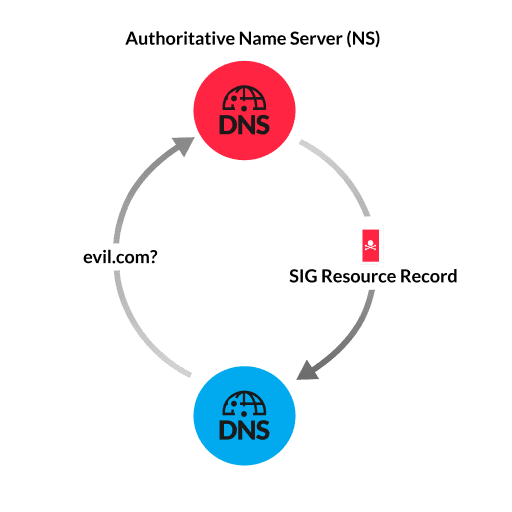
SIGRed is a vulnerability in Windows DNS Server. To exploit this vulnerability, the attacker first sets up a simple DNS infrastructure that includes a registered domain and a DNS server that acts as the authoritative name server (NS) for that domain. When the victim tries to resolve the attacker-controlled domain or sub-domain, the victim sends a DNS query that is ultimately received by the attacker-controlled NS. The NS responds to the victim by sending a SIG resource record, which is a legacy record type for holding digital signatures. Instead of including a small digital signature, however, the attacker includes a large, compressed payload. The Windows DNS implementation on the victim assumes that the maximum SIG record payload size is smaller than a threshold of approximately 65,000 bytes, without considering how decompression affects the SIG record payload size. (The maximum size of a DNS response over a TCP connection is 65,536 bytes, and records typically contain compressed payloads to reduce DNS response size.) Because the decompressed SIG record payload is larger than 65,000 bytes, the DNS resolver allocates too little memory on the heap memory of the victim to process the DNS response. When data is copied into the buffer, a heap-based overflow occurs. Malicious, arbitrary code can now run on the Windows DNS server with Local System Account privileges.
Network analysis and visibility solutions remain underrepresented in enterprises. Find out why in this preview of a new Wave report.
ExtraHop® Named a Leader in First-Ever Gartner® Magic Quadrant™ for Network Detection and Response
Visit this resource for more information.
This analysis exposes the critical link between an organization's lack of internal visibility and the escalating cost of compromise, demanding an urgent re-evaluation of how core business assets are protected.
Learn why you need to be wary of the claims certain network detection and response providers make about their coverage against the MITRE ATT&CK framework.
Learn how NDR from RevealX helps security teams detect and investigate more adversary TTPs in the MITRE ATT&CK framework than rule-based tools.
