- Platform
- Solutions
- Modern NDR
- Resources
- Company
Platform
Modern NDR
Resources
Company
DETECTION OVERVIEW
Risk Factors
An unauthenticated attacker with access to a vulnerable Manage Engine Desktop Central server can remotely run arbitrary code on the server. A successful exploit can result in the attacker gaining control of the server and launching additional attacks on network devices, deploying ransomware, or moving laterally across the network.
Category
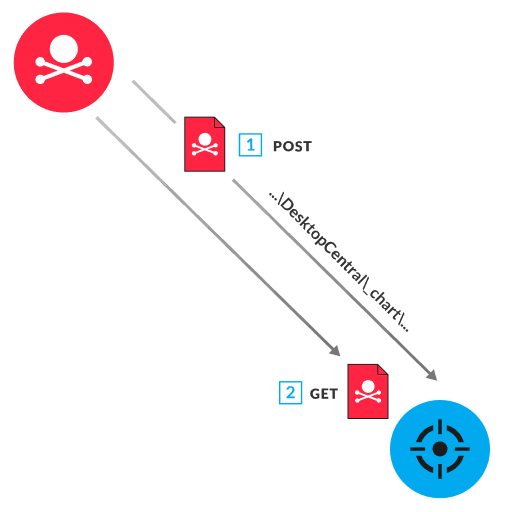
The ManageEngine Desktop Central service acts as a central server to help manage connected devices, such as workstations, servers, and phones, within an enterprise environment. Desktop Central contains a vulnerability that allows untrusted data in uploaded files to be processed and run as code on the ManageEngine server. To exploit this vulnerability, the attacker submits a POST request to upload a malicious file to a specific folder (\ManageEngine\DesktopCentral_Server\webapps\DesktopCentral\_chart) (1). The attacker then sends a GET request to run the malicious file (2). The malicious code runs on the ManageEngine server with system, or root, privileges. The attacker can then perform additional attacks, such as sending malware or ransomware to connected devices across the network.
ExtraHop spoke to three leading cyber intelligence experts to refine its forecast for RaaS royalty in 2025.
The 2025 ExtraHop Global Threat Landscape Report examines the expanding attack surface and evolving tactics being used by threat actors
If you think ransomware is bad now, cybersecurity experts warn it’s only going to get worse as 2024 wears on and the US general election approaches. Tile description:
Network analysis and visibility solutions remain underrepresented in enterprises. Find out why in this preview of a new Wave report.
ExtraHop® Named a Leader in First-Ever Gartner® Magic Quadrant™ for Network Detection and Response
Visit this resource for more information.
This analysis exposes the critical link between an organization's lack of internal visibility and the escalating cost of compromise, demanding an urgent re-evaluation of how core business assets are protected.
Learn why you need to be wary of the claims certain network detection and response providers make about their coverage against the MITRE ATT&CK framework.
Learn how NDR from RevealX helps security teams detect and investigate more adversary TTPs in the MITRE ATT&CK framework than rule-based tools.
