- Platform
- Solutions
- Modern NDR
- Resources
- Company
Platform
Modern NDR
Resources
Company
DETECTION OVERVIEW
Risk Factors
An attacker with network access to an affected Windows 10 device can exploit this Microsoft Server Message Block 3.1.1 (SMBv3) vulnerability. A highly skilled attacker must create a specially-designed SMBv3 packet that bypasses Windows safeguards. If successful, an unauthenticated attacker can have a large impact by creating a denial-of-service (DoS) scenario or running arbitrary code to gain complete control of a device.
Category
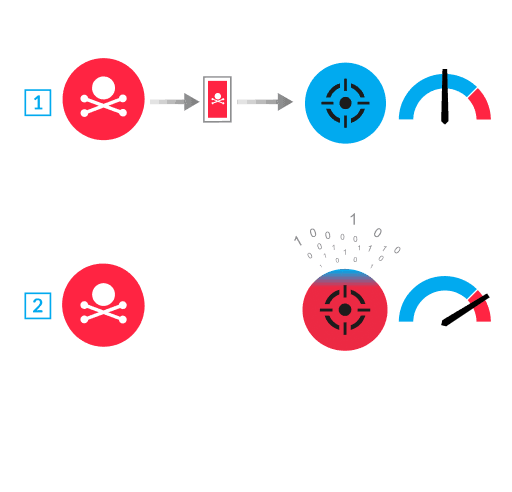
With this type of attack, the attacker creates a specially-designed SMBv3 packet with modified parameter values about the compressed data size of the payload and offset. The victim device only allocates a small amount of memory based on these values (1), and the victim ends up overwriting items in kernel memory with the malicious payload (2). The results vary depending on the attacker's objective: the attacker can cause a denial-of-service (DoS) by completely crashing the device or they can run arbitrary code in the kernel.
Install relevant patches for affected software and server versions
Disable SMBv3 compression if unable to apply the patch
Block TCP traffic on port 445 at the network perimeter
Network analysis and visibility solutions remain underrepresented in enterprises. Find out why in this preview of a new Wave report.
ExtraHop® Named a Leader in First-Ever Gartner® Magic Quadrant™ for Network Detection and Response
Visit this resource for more information.
This analysis exposes the critical link between an organization's lack of internal visibility and the escalating cost of compromise, demanding an urgent re-evaluation of how core business assets are protected.
Learn why you need to be wary of the claims certain network detection and response providers make about their coverage against the MITRE ATT&CK framework.
Learn how NDR from RevealX helps security teams detect and investigate more adversary TTPs in the MITRE ATT&CK framework than rule-based tools.
