- Platform
- Solutions
- Modern NDR
- Resources
- Company
Platform
Modern NDR
Resources
Company
DETECTION OVERVIEW
Risk Factors
An attacker with internet access to a Citrix ADC or Gateway device can easily scan the device for known vulnerabilities. The attacker is able to collect configuration information from the scanned device and learn whether the device is vulnerable to remote code execution (RCE).
Category
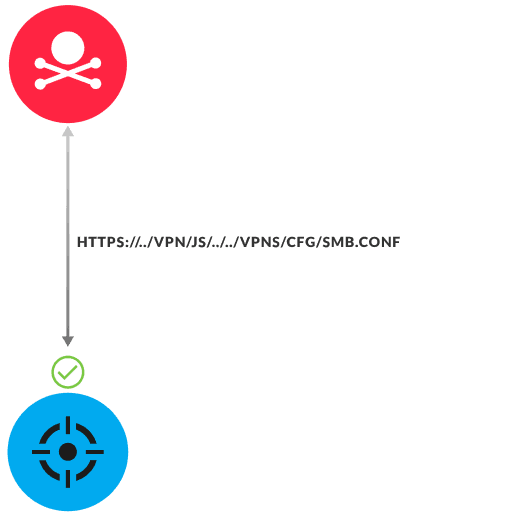
Several Citrix products contain a vulnerability that enables an attacker to traverse restricted directory paths and remotely run arbitrary code on the device. Before launching a full attack, the attacker scans the target by attempting to access the smb.conf file to confirm if the vulnerability exists. The attacker tests to see whether the path https://../vpn/js/../../vpns/cfg/smb.conf can be traversed without receiving access denied errors. If successful, the attacker can access configuration data from other files, and potentially upload and run scripts from this directory.
Upgrade to a fixed version, or configure affected devices to mitigate CVE-2019-1978
