Stopping Identity-Based Attacks Before They Steal Your Crown Jewels
Back to top
November 5, 2025
Stopping Identity-Based Attacks Before They Steal Your Crown Jewels
In a brazen daylight heist on October 19, 2025, thieves stole eight pieces of 19th-century French crown jewels worth an estimated $102 million from the Louvre's Apollo Gallery. Using a truck-mounted ladder to access a second story window, the thieves, disguised as construction workers, smashed display cases and escaped on motorbikes within seven minutes.
The incident sparked outrage over major security lapses at the museum and led to questions about how the thieves were able to enter, operate, and exit the museum during regular hours with visitors present.
Just as the Louvre heist highlights vulnerabilities in physical security, ExtraHop's identity capabilities provide crucial defenses against digital "heists" by securing privileged user accounts, which are often attackers' most valuable targets.
Privileged User Accounts are Attackers’ Ultimate Entry Point
Privileged user accounts are prime targets for cybercriminals. Should these accounts be compromised, they could provide extensive access to your organization's most critical assets.
Gaining control of a privileged or influential executive account, an account that possesses administrator or "root" access, offers maximum control to attackers, allowing them to bypass or disable security measures. These accounts also serve as gatekeepers to sensitive data, enabling lateral movement across the network so bad actors can evade detection, escalate their access to gain complete control, and carry out large-scale attacks like data breaches or ransomware with stealth.
Privileged Accounts Quickly Become Launchpads for Cyberattacks
Initial access starts when attackers compromise user accounts primarily through targeted social engineering attacks and technical exploitation of credentials. These methods leverage the users authority, access to sensitive data, and busy schedules to facilitate access and avoid scrutiny.
When attackers disguise themselves as an authorized user using compromised credentials, similar to the jewelry thieves dressing up as construction workers, and use legitimate tools, they can easily evade detection and get in and out with the sensitive data they are looking for before anyone notices.
*https://securis.com/news/privileged-access-management/
*https://identitymanagementinstitute.org/privileged-account-management-pam/#:~:text=Industry%20analysts%20estimate%20that%20up,password%20for%20several%20different%20accounts.
Statistics show that a large percentage of data breaches come from misuse of privileges, insider threats, and password hacks, which highlights the risks that come with elevated access. Proactive oversight is crucial to minimize potential damage and to make sure you are alerted when a detection related to a high-value user occurs.
Human Error and Technical Vulnerabilities Make Identity Attacks Inevitable
Adversaries launch sophisticated identity attacks by strategically targeting crucial authentication and authorization systems or by illicitly obtaining valid user credentials.
Human error poses a major risk, with attackers frequently leveraging social engineering and phishing to trick individuals into revealing sensitive information, and taking advantage of poor cyber hygiene practices like weak, reused passwords for credential stuffing and password spraying attacks. Add in MFA fatigue and insider threats, whether malicious or negligent, and threat actors can get in with ease.
Technical and system vulnerabilities provide further avenues for exploitation, stemming from inadequate authentication mechanisms and misconfigured identity and access management (IAM) systems. Protocol weaknesses, such as those in Kerberos, and session hijacking allow attackers to bypass security measures and gain control.
How ExtraHop Solves the Identity Problem
ExtraHop's identity capabilities give security teams the clarity and context needed to understand who is behind network activity. This enables more accurate detections, faster triage and investigations and stronger security outcomes. By making identity a pivot point, security teams can trace user activity across on-prem and cloud environments, regardless of where they authenticated. This provides a fuller picture, highlighting unusual behavior, surfacing high-risk accounts and devices, all while reducing tool hopping so analysts can focus on defending their organization’s most valuable assets.
Keep Track of Your High-Value Assets
ExtraHop identifies and prioritizes "high-value devices" within your network, which are critical assets providing essential services like authentication.
These devices are automatically detected and assigned a higher risk score, but you can also manually designate any device as high-value for increased analysis and monitoring. This prioritization ensures that security detections involving these critical assets receive urgent review and deeper scrutiny through Advanced Analysis, helping you quickly identify and respond to potential threats.
Once an asset is designated as high-value, ExtraHop triggers and prioritizes alerts based on its detection of anomalous activity by applying advanced machine learning and detection rules to network traffic involving those assets. Alerts related to high-value assets are given higher priority to help analysts focus on the most critical threats.
Stop Attackers in their Tracks: Flag Suspicious User Behavior
Analysts can quickly trace suspicious behavior by starting with a user-enriched detection, viewing their device interactions, protocol usage, and triggered detections – all within a single interface. The ExtraHop RevealX platform excels at detecting lateral movement, tracking accounts across internal systems via protocols like SMB, RDP, NTLM, or Kerberos.
Filtering by user tags helps prioritize investigations, allowing teams to focus on high-risk accounts and reduce noise from less critical service accounts, leading to faster, more confident resolutions.
For suspected compromises, security analysts can rapidly assess the "blast radius" by identifying accessed systems, associated devices, and exposed data to take action.
Automate Identity-Based Triage and Investigations
When a privileged user account is linked to a network detection and response (NDR) detection, our advanced smart triage system automatically highlights, recommends, and prioritizes it within the security platform. This intelligent automation ensures that the most critical incidents involving high-value targets are brought to the immediate attention of your security teams.
The ExtraHop RevealX platform is an identity-aware NDR designed with streamlined workflows that empower security professionals to fully leverage this enriched user data. By providing comprehensive context around privileged user activities and their connection to detected threats, this information becomes a central pivot point for in-depth investigations. This allows you to quickly understand the scope of an incident, identify potential attack vectors, and determine the necessary response actions, significantly reducing investigation times and improving overall incident response efficacy.
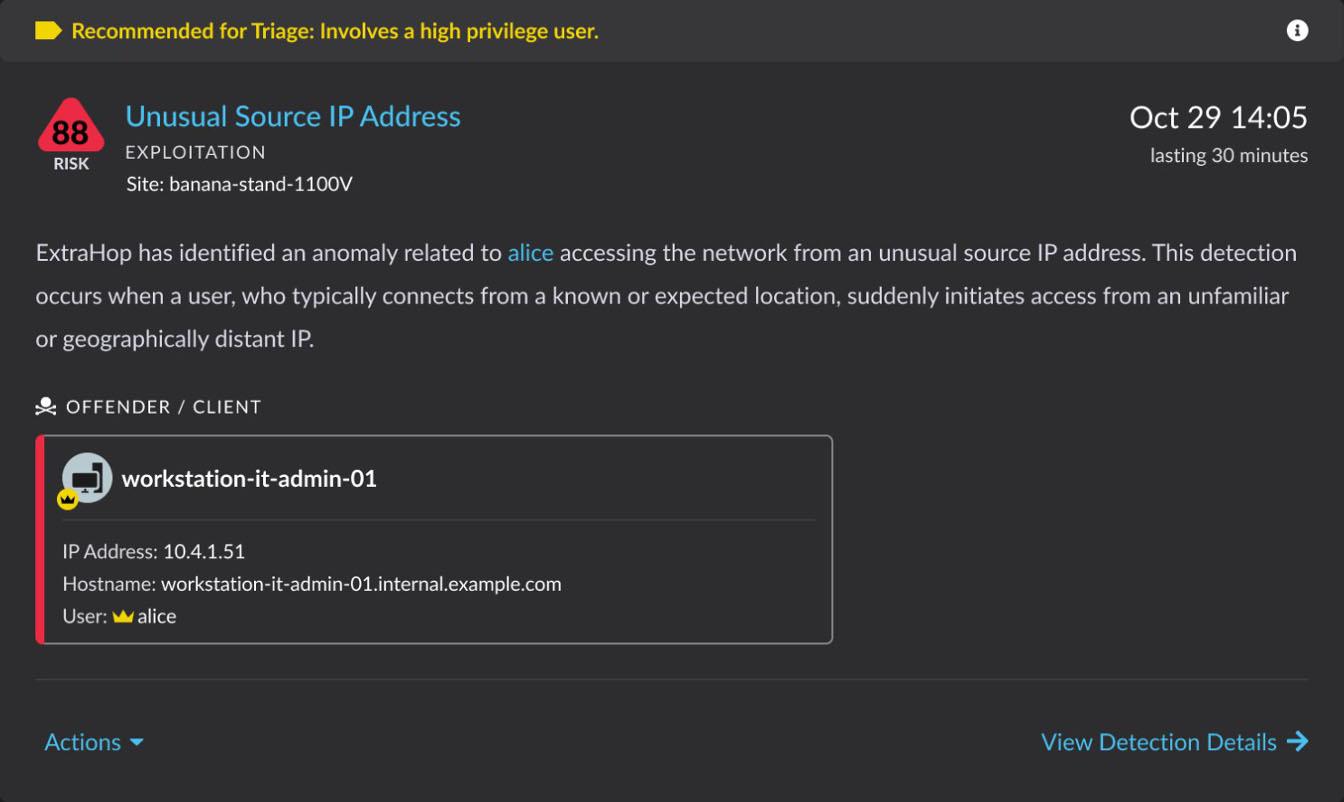
Designate privileged and influential users within RevealX to prioritize identity-based detections for triage.
Schedule a demo with one of our experts to see our latest identity threat investigation capabilities.
Discover more

Senior Product Marketing Manager
Alexis is a Senior Product Marketing Manager at ExtraHop. She has been marketing cybersecurity and digital investigation products for the past 20 years focused on go-to-market strategy, new product launches, and content development.
Outside of work, Alexis enjoys volunteering for a teen mental health non-profit, traveling, and reading science fiction.
Follow Alexis on LinkedIn: https://www.linkedin.com/in/arobbins/









