 Blog
Blog
ExtraHop Contributes Network Security Expertise to MITRE ATT&CK Framework
ExtraHop becomes first and only NDR vendor to contribute to ATT&CK
Chase Snyder
June 29, 2021
The MITRE ATT&CK framework has become a valuable tool for security teams to identify gaps in their threat detection capabilities. When ExtraHop added MITRE ATT&CK mapping into our Reveal(x) product interface, our customers were delighted. Many immediately wanted to learn more about how network data is used for threat detection and response.
In the latest update, version 9, MITRE has updated ATT&CK to include new attack techniques and offer a greater understanding of the network as a data source, with input from ExtraHop. Previously, network data was underrepresented in the ATT&CK framework. Most tactics, techniques, and procedures (TTPs) relied on endpoint monitoring and activity logs (both of which are important and still heavily represented) for threat detection and response. By contributing this expertise to the MITRE ATT&CK framework, ExtraHop will help security teams fill one of the biggest security tooling and visibility gaps: the network.
ExtraHop continuously strives to help our customers secure their environments more effectively. Our expertise and long history in identifying network-detectable cyberattack behaviors has led us to be the first and only network detection and response (NDR) provider to be listed as a contributor to the MITRE ATT&CK framework. We were also the first NDR product to natively integrate ATT&CK into our product's interface. NDR is a vital tool to detect and respond to modern advanced threats, and we continue to invest in research and development to help the SOC take back the advantage from cyberattackers.
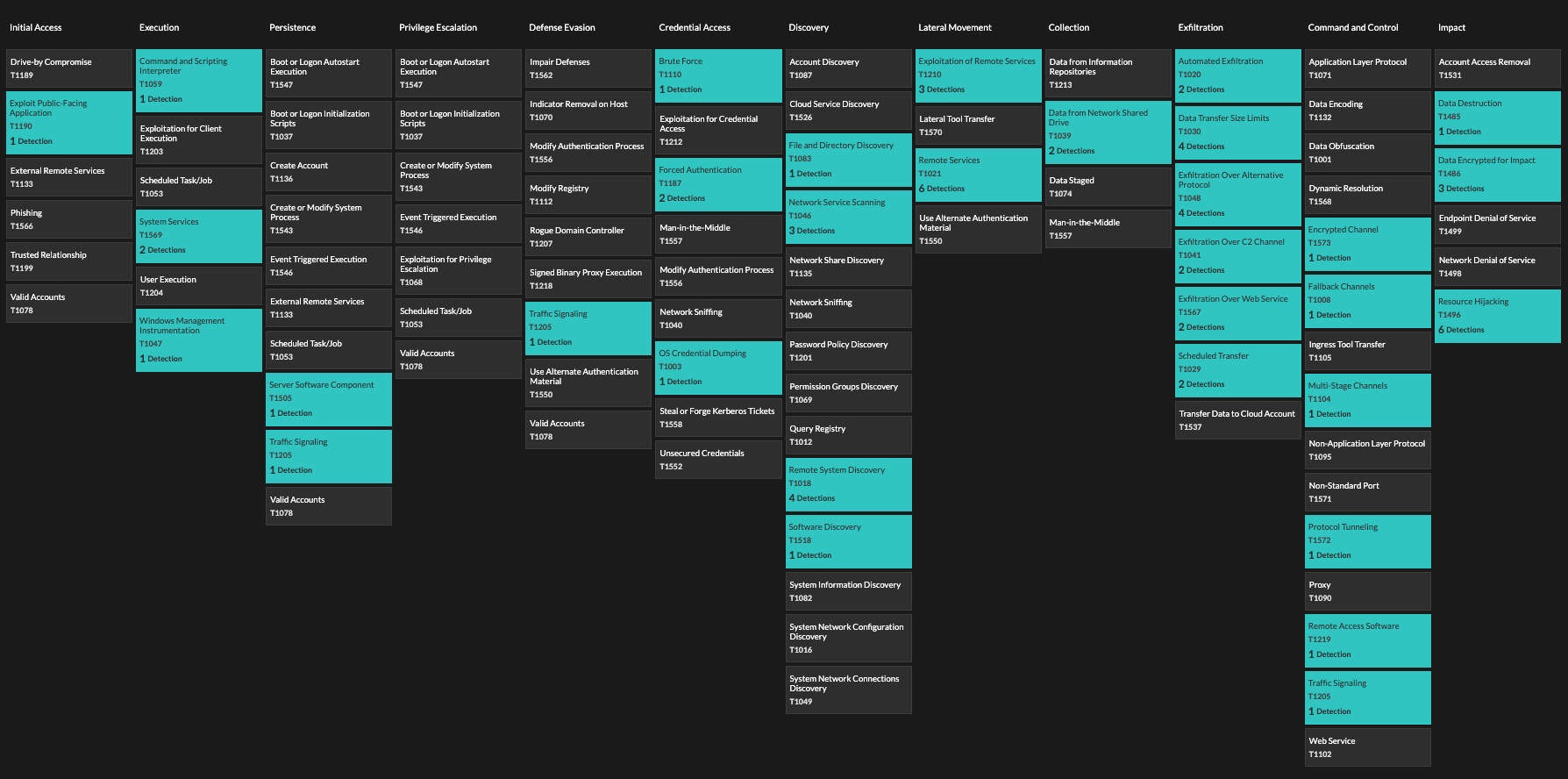
The MITRE ATT&CK matrix in the ExtraHop Reveal(x) interface.
Attackers Can't Hide in the Network
Recent high-impact cyberattacks, such as SUNBURST and the DarkSide ransomware attack, have highlighted major gaps in the threat detection and response capabilities of many organizations.
Attackers have grown more sophisticated at evading detection by endpoint detection and response (EDR) agents and log-based security information and event management (SIEM) solutions. Furthermore, endpoint and log-based solutions can be difficult to deploy with complete coverage. The proliferation of remote work, IoT, and cloud adoption has exacerbated the difficulty of achieving and maintaining complete security coverage.
Attackers evaded detection by avoiding secured or monitored endpoints. This gave them enough dwell time to establish persistence, move laterally, and ultimately cause much more damage than they would have if they had been detected sooner.
The extensive use of common network protocols for command and control, lateral movement, and data exfiltration makes the DarkSide and SUNBURST attacks highly detectable on the network. These attackers used commonly abused and under-monitored protocols such as DNS and RDP for command and control and lateral movement, which can be caught with appropriate deployment of NDR.
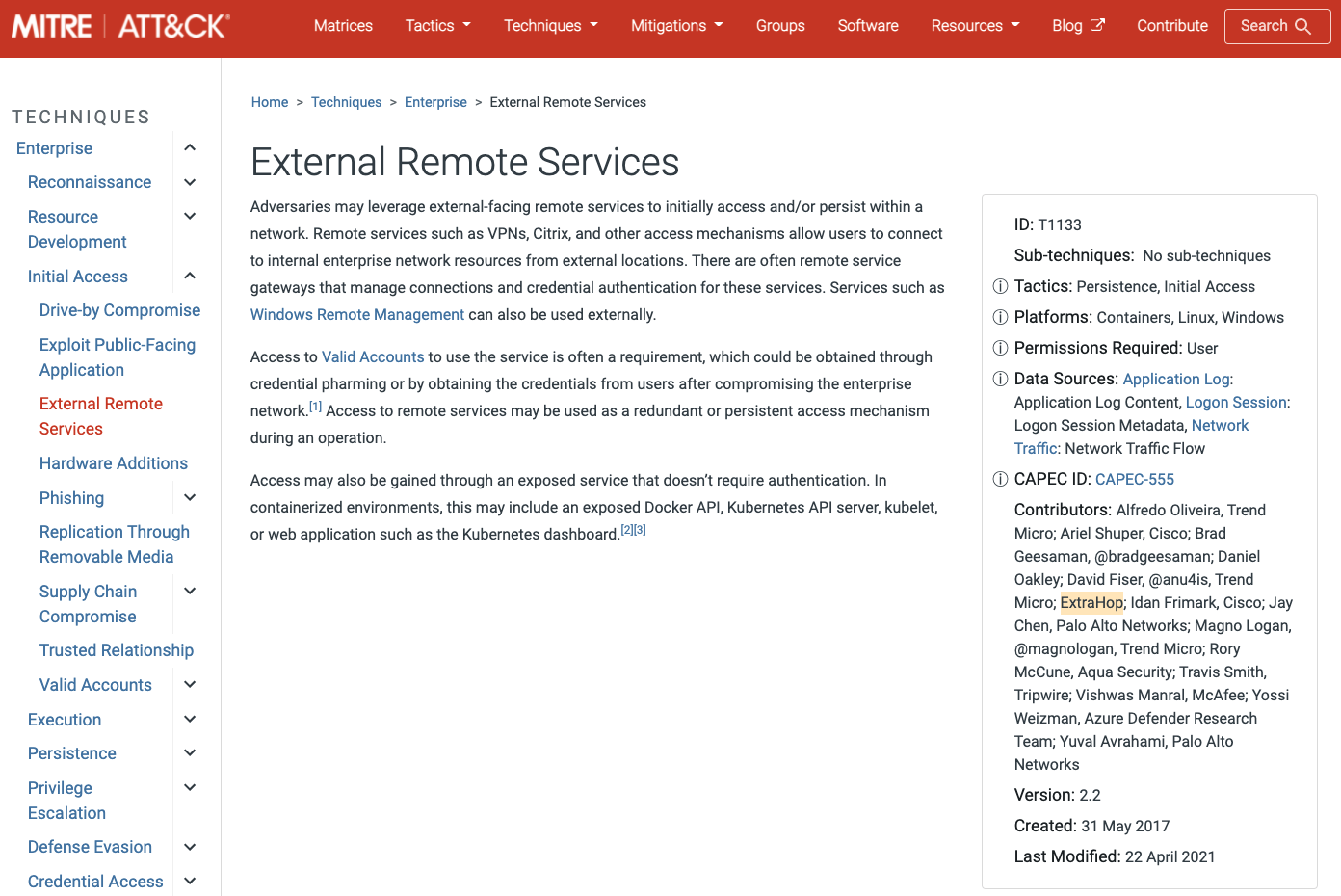
ExtraHop is listed as a contributor on External Remote Services and several other techniques and subtechniques in the MITRE framework.
Real-time observation of network traffic, combined with traffic decryption, protocol parsing, and ML behavioral modeling helped many organizations reduce or entirely avoid the impacts of these attacks.
NDR Does What Other Tools Can't: Covert Detection of Unknown Threats
NDR is not a replacement for SIEM or EDR, which have vital roles to play—instead security teams should consider integrating NDR with SIEM. NDR provides visibility into activity these other tools can't see. Furthermore, NDR is the only security tool that operates entirely covertly. Attackers can tell if there is an EDR agent on an endpoint they are attacking and can choose to try another path. Attackers routinely erase or modify activity logs to reduce or eliminate SIEM visibility.
Attackers can't tell if their network traffic is being passively watched. They can't tell if their network transactions are being decrypted or if their C2 traffic is flagged by behavioral models.
Furthermore, network traffic is universal in the enterprise. Even notoriously insecure and rapidly proliferating IoT devices, which can't necessarily support a monitoring agent or activity logging, cannot avoid talking on the network. Attackers who try to exploit the growing attack surface caused by IoT and remote devices can still be caught with NDR.
The Network Is Cybersecurity's Next Frontier
The inclusion of more network attack behaviors in the ATT&CK framework serves as both a useful tool and a strong signal for SOC teams: NDR is a vital tool for the SOC. Without NDR you've got a blind spot that attackers know how to exploit. ExtraHop is continuing to identify more ways of detecting attack techniques on the network, and we're working with MITRE to include this information in the ATT&CK framework so that security teams worldwide can benefit.
For the past several years, security teams have heavily focused on operationalizing their EDR and SIEM solutions. As more advanced threats take advantage of network blind spots, the importance of NDR as a foundational tool and data source for the SOC will rise. Those SOC teams that stay ahead of the curve in NDR adoption will find themselves taking back the upper hand from cyberattackers, and delivering a competitive advantage for the businesses they defend.
To quote Rob Joyce, Director of Cybersecurity at the National Security Agency: "[An attacker's] worst nightmare is that out-of-band network tap that really is capturing all the data, understanding anomalous behavior that's going on, and someone is paying attention to it. You've gotta know your network. Understand your network, because [the attacker] is going to."
To learn more about the updates to the MITRE ATT&CK framework, including network-focused techniques and ExtraHop's contributions, you can read MITRE's release notes for v9 of MITRE ATT&CK.
This three minute video will provide you with a quick overview of how MITRE ATT&CK is integrated into the Reveal(x) NDR product UI.
Our whitepaper on the MITRE ATT&CK framework will give you a deeper dive into attack tactics, techniques, and procedures that are detected by Reveal(x) NDR.
Discover more
