 Blog
Blog
What is DNS Tunneling and How to Protect Against It
Kirsten Gantenbein
October 19, 2020
Domain Name System (DNS) is an essential protocol that keeps the internet running by translating human-readable domain names into IP addresses. Many services would grind to a halt without the enormous number of DNS translation queries that occur constantly, and so DNS traffic is widely trusted and often ignored.
But DNS is more than a translation tool for domain names. DNS queries are also capable of shuttling small amounts of data between two systems. Unfortunately, this makes DNS an appealing vector for attacks that can secretly transport commands and exfiltrate data through DNS tunneling.
What Is DNS Tunneling?
DNS tunneling is a difficult-to-detect attack that routes DNS requests to the attacker's server, providing them with a covert command and control channel, and data exfiltration path.
Let's start with a compromised device: a user downloaded malware or an attacker exploited a vulnerability to deliver a malicious payload. If the attacker wants to maintain contact with the compromised device (to run commands on the victim device or exfiltrate data), they can establish a command-and-control (C2) connection. C2 traffic must be able pass through network perimeter defenses and evade detection while crossing the network.
DNS is a good candidate for establishing a tunnel, which is a cybersecurity term for a protocol connection that encapsulates a payload that contains data or commands and passes through perimeter defenses. Essentially, DNS tunneling hides data within DNS queries that are sent to an attacker-controlled server. DNS traffic is generally allowed to pass through perimeter defenses, such as firewalls, that typically block inbound and outbound malicious traffic.
To establish a DNS tunnel, the attacker registers a domain (baddomain.com) and sets up a C2 server as the authoritative name server for baddomain.com. The malware or payload on the compromised device sends a DNS query for a subdomain that represents an encoded communication (base64encodedcommunication.baddomain.com). The query is eventually routed by a DNS resolver (through root and top-level domain servers) to the C2 server. The C2 server then sends a malicious DNS response that includes data (such as a command) to the compromised device, passing undetected through the perimeter. Over time, the attacker can continue C2 activity or exfiltrate data through the DNS tunnel.
How to Detect DNS Tunneling
A compromised device might continuously send DNS queries to beacon, or ping, the C2 server for commands. Data exfiltration might also result in many DNS queries because a query can hold only a small amount of data. Overall, DNS tunnel traffic can be noisy. But typical DNS network traffic can also be noisy, making it difficult to distinguish suspicious or unusual DNS queries from the legitimate ones.
ExtraHop Reveal(x) automatically detects unusual changes in DNS traffic based on device behavior over time, surfacing queries that should be investigated. A defender can investigate the DNS query from the detection card.
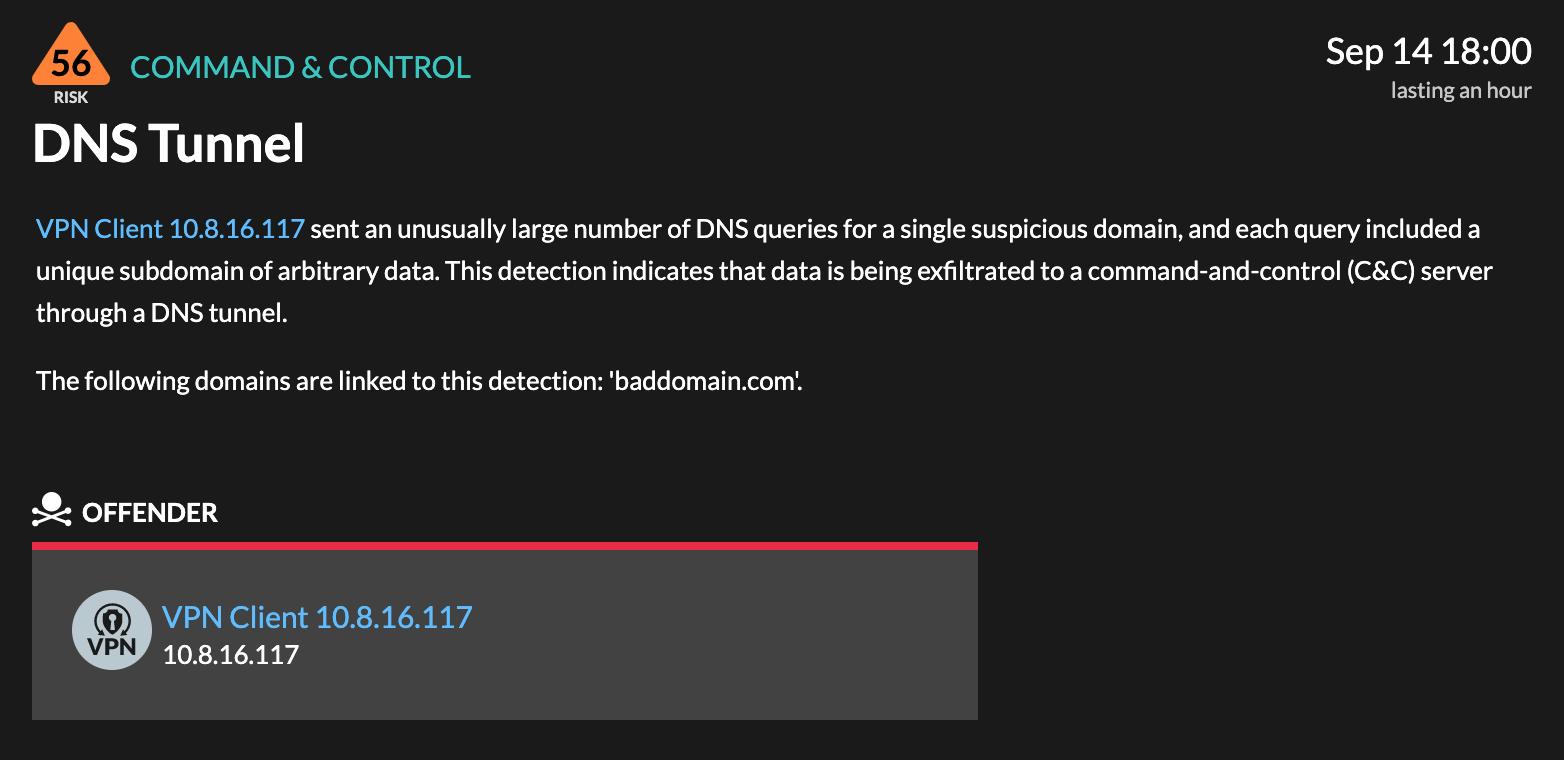
Investigate DNS Queries
DNS queries include record types, which help DNS servers retrieve the correct information about the requested domain. For example, an "A" record type requests the IPv4 address for a domain name. Attackers might encode data into a subdomain name of an A record type, such as base64encodedgibberish.baddomain.com:
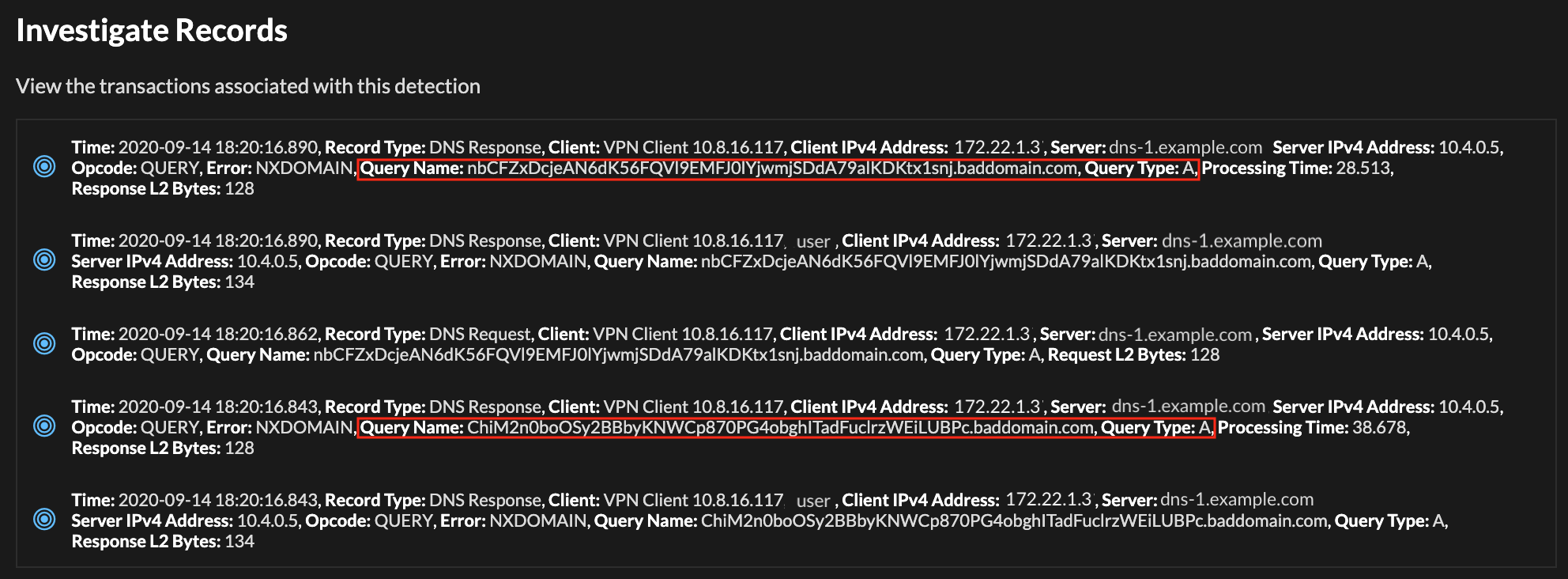
The host queries include A records and suspicious characters instead of a human-readable subdomain.
How to Prevent DNS Tunneling
Because DNS is an essential service, it can be difficult to block. But a defender might be able to identify suspicious domains and IP addresses from threat intelligence matches. DNS traffic that is sent to known malicious endpoints and domains can be blocked at the perimeter. Also, internal clients can be configured to send all queries to an internal DNS server that filters or blocks suspicious domains.
Keep in mind that suspicious domains might be short-lived to avoid detection. Staying vigilant for suspicious domains, monitoring DNS traffic, and reporting suspicious domains to threat intelligence platforms, can help reduce the effectiveness of DNS tunnels in abetting malicious C2 activity.
Discover more
