 Blog
Blog
How Attackers are Leveraging the Log4j Vulnerability Six Months Later
Jamie Moles
June 30, 2022
Over six months ago, on December 14th, a little-known but ubiquitous logging utility, log4j embedded deep into the software supply chain caused a cybersecurity stir when a zero-day vulnerability that allows remote code execution attacks—enabling an attacker to gain full server control—was disclosed. It was widely reported, with news outlets generating widespread awareness of the explosive vulnerability that was dubbed Log4Shell. Security teams responded to the supply chain attack by scrambling to update affected devices.
After the Log4Shell disclosure, defenders had a difficult task ahead: Log4j is extremely common in Java-based apps, including iCloud, the popular game Minecraft, and numerous others. This made it difficult for organizations and individuals to know if and where the supply-chain dependency was running on their network, and attackers knew that just one unpatched device is enough to gain a foothold.
Log4j Vulnerabilities Six Months Later
Broad awareness and quick action can be attributed to the fact that no massive breaches have been reported as a result of Log4j. Despite the quick response, Log4j has become a standard target for vulnerability scanners and hacker toolkits—and is even built-in to a number of botnets. I would expect that continuous scanning for vulnerable systems may continue to occur for a long time as criminals use automation to look for easy targets.
The Data:
Since its disclosure, ExtraHop tracked scan attempts for the Log4j vulnerabilities month over month. ExtraHop data shows that cybercriminals continue to scan for Log4j vulnerabilities, despite a patch being available for over six months. While the volume of attempts has declined recently, February, March, and April were big months for exploit scanning, proving that cybercriminals are capitalizing on the widespread nature of this vulnerability.
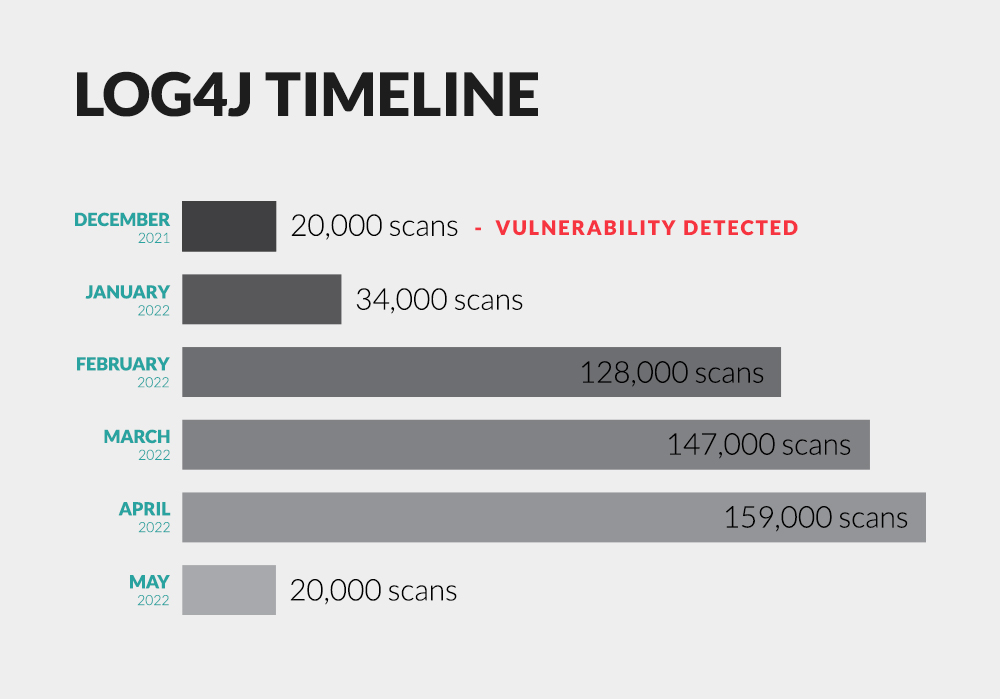
While the recent dip in scanning attempts may signal a slowdown, the massive drop may be due to law enforcement's shut down of botnet networks. We'll see continuous scanning for vulnerable systems for a long time now as criminals take advantage of their automated tools to target low-hanging fruit.
The Top Targeted Industries
Among the industries targeted, ExtraHop found that a disproportionate volume of scans targeted the financial services sector. Financial services organizations made up 20% of the sample set, yet accounted for 49% of the scan attempts. This data shows that the scans are likely becoming more targeted, focusing on industries where cybercriminals expect a bigger payoff for their efforts. Financial services are an attractive target due to the massive potential payoffs from hacking organizations who handle vast amounts of wealth.
The fact that scans are focusing on the financial sector is consistent with the fact that finance is the most breached industry according to the 2022 DBIR: The report found that financial institutions suffered 690 breaches among a total of 5,212 breaches reported across 21 industry sectors.
The next biggest scanning target according to ExtraHop data is healthcare, which accounted for 17% of the sample set but 11% of the scan attempts. Healthcare, which has been a consistent target for attackers over the past decade, was the fourth most breached industry, according to the 2022 DBIR.
An 'every dollar spent on positive patient outcomes is a dollar well spent' mindset may be the reason why healthcare organizations remain among the top victims of cybercrime. A recent survey conducted by HIMSS indicates that healthcare organizations are allocating 6% or less of their IT budget toward cybersecurity.
Identifying Signs of Log4j Compromise
The net takeaway here is that organizations should continue to stay vigilant to prevent attackers from successfully discovering unpatched Log4j access points. While scanning attempts have recently dropped, the numbers may trend toward a temporary dip rather than an overall downward trend, making continued security efforts necessary.
While a previous article offers a detailed technical explanation of how Log4j attacks work and how to detect them, the basic premise is that, for a Log4j exploit attack to proceed, the vulnerable application must be tricked into reaching out to an external server. Established network baselines can help identify normal vs anomalous behavior, helping to identify signs of compromise. Understanding normal network behavior gives organizations the ability to quickly identify IoCs associated with this flaw. This allows security teams to stop a breach, even if attackers succeed in identifying and exploiting unpatched Log4j vulnerabilities.
Discover more