 Blog
Blog
Why Conventional Wisdom Hasn't Stopped or Even Slowed Ransomware
May 20, 2022
Ask any other security leader, they'll tell you ransomware is their top threat initiative, and the board is asking what they are doing about it. Read recommendations from analysts, government agencies, and vendor's councils on stopping the ransomware menace, and repeated themes persist: better access controls, regular patch management, more phishing training, and having backups ready.
Despite conventional wisdom, implementation of these reasonable and wise requirements hasn't slowed the frequency or dampened ransomware's crushing impacts on victims' businesses. Meanwhile, counting on cyber insurance and frequent backups only offers partial relief after the collateral damage is done.
What these pearls of wisdom miss is that prevention often fails against motivated extortionists: There is more to the fight than preventing initial access and then falling back to recovery.
Modern ransomware is now carried out in a three-part playbook:
- Opening (initial access)
- Midgame (post compromise)
- Endgame (extortion, get paid)
Each phase has its specialization experts and a supporting tooling ecosystem. Fighting two of the three rounds hasn't been an effective strategy; defenders have to battle at each stage to beat back the extortionists.
The attackers control the cadence and hold the advantage at the opening. Yes, intrusions are a terrifying thing to consider. Still, they don't spell doom: Visibility and response inside the perimeter are your best hope to prevent crippling damage from the ransomware menace.
But first, let's explore why initial access prevention inevitably fails and reliance on recovery alone is surrendering to the collateral damage of ransomware.
Why Initial Access Prevention Fails
Shift left is a key security mantra. The hope is to stop the attacker before they get a foothold by blocking their initial moves with firewalls, IAM, anti-phishing training, EDR, and a slew of other preventive controls. Unfortunately, there is a narrative in the security community called the defender's dilemma, an uncomfortable downer for shift left. It points to the reality that the attacker has the advantage at the perimeter because the attacker controls the what, when, and how they attack, tweaking as they go. Whereas the defender has to have all the controls in place before the attack and be right 100% of the time to win. The defender's dilemma warns of the inevitable failure of preventative defenses against a persistent attacker.
Is it true? As an industry, we hate to accept it, but history repeatedly proves it to be so. Let's consider a couple of alarming facts:
(1) 4.8% out of 6.6 million users from 23K companies, after one full year of phishing training, will click the bait. Based on a 4.8% click rate, if an attacker sends 100 well-crafted emails, they have a 99.27% chance that at least one user will open the bait (math here). So, what hope is there to prevent initial access as long as people are part of the equation?
(2) 93% of all penetration test results in a successful intrusion, without using social engineering techniques. Keeping in mind pentesters are on a short timeline, and have limiting rules of engagement, the probability of success for a financially motivated attacker with patience is even higher.
This means that while any security team would prefer to stop an attacker at the beginning of the kill chain—it makes more practical sense to take on attackers where you have the advantage. The fact is that intrusions are inevitable against persistent attackers, making the perimeter only the first line of defense against more easily deterred attackers. Investments and expectations may need to be adjusted for this reality.
The ransomware defender's higher ground is actually in the midgame, but we will get to that after we look at the conventional widsom typically applied to part three, their endgame.
Why Backups and Cyber Insurance Aren't Enough
Having backups and layering cyber insurance is wise and necessary. However, the math doesn't match "do this, get that" with ransomware. This is because the extortion demand doesn't equal the damage caused by modern ransomware, where extortionists apply unfair game theory to ensure you will pay.
For example, in 2021, the average ransom payment, negotiated down from the staggering millions of dollars demanded, was $170K. However, in the same year, the average impact from ransomware was $1.85M.
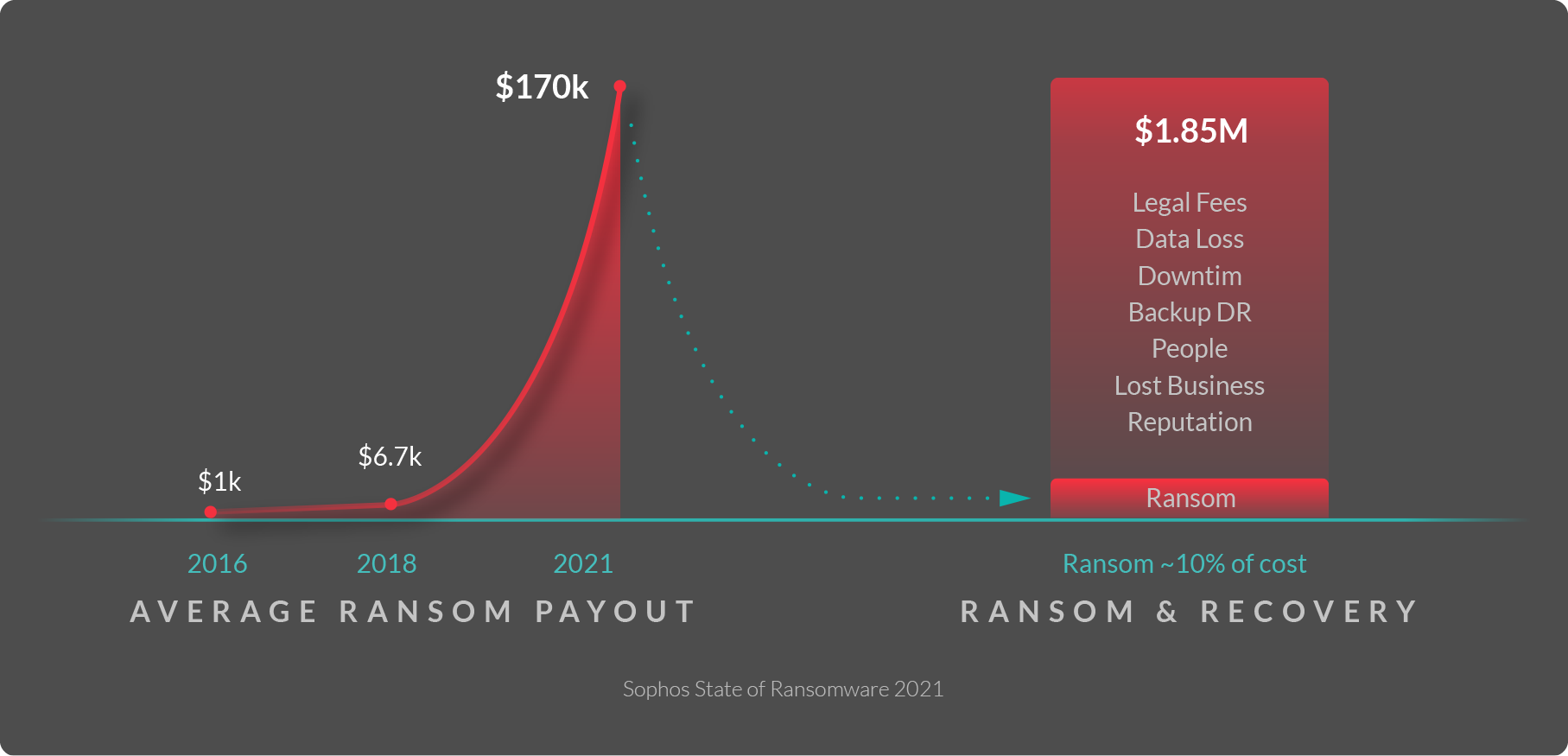
During the crisis phase, the media, insurance-sponsored negotiators, and likely your business leaders will focus on the shocking ransom demand. No question having backups and cyber insurance are critical parts of your ability to negotiate. Although, blackmail feels weird, dirty, shameful, it also accounts for only 10% of the total weighted damage. Pay, don't pay, the impact of downtime, lost business, and other indirect impacts from reputational damage and recovery expenses have to be dealt with once the ransomware opening kicks off.
The only way to be fully resilient against ransomware is to stop the intruder before the data is encrypted and the ransom note is delivered.
As we can see, hoping perimeter defenses hold, then falling back to recovery plays into the hands of ransomware.
How to Stop Ransomware Before the Encryption Starts
The Ransomware Midgame
In the midgame, the ransomware intruder lands blind into the victim's infrastructure, then sets out to meet their objectives. Their necessities and tooling to discover and pivot toward critical assets are documented in their leaked playbooks and insights shared by incident responders'post-mortem reports.
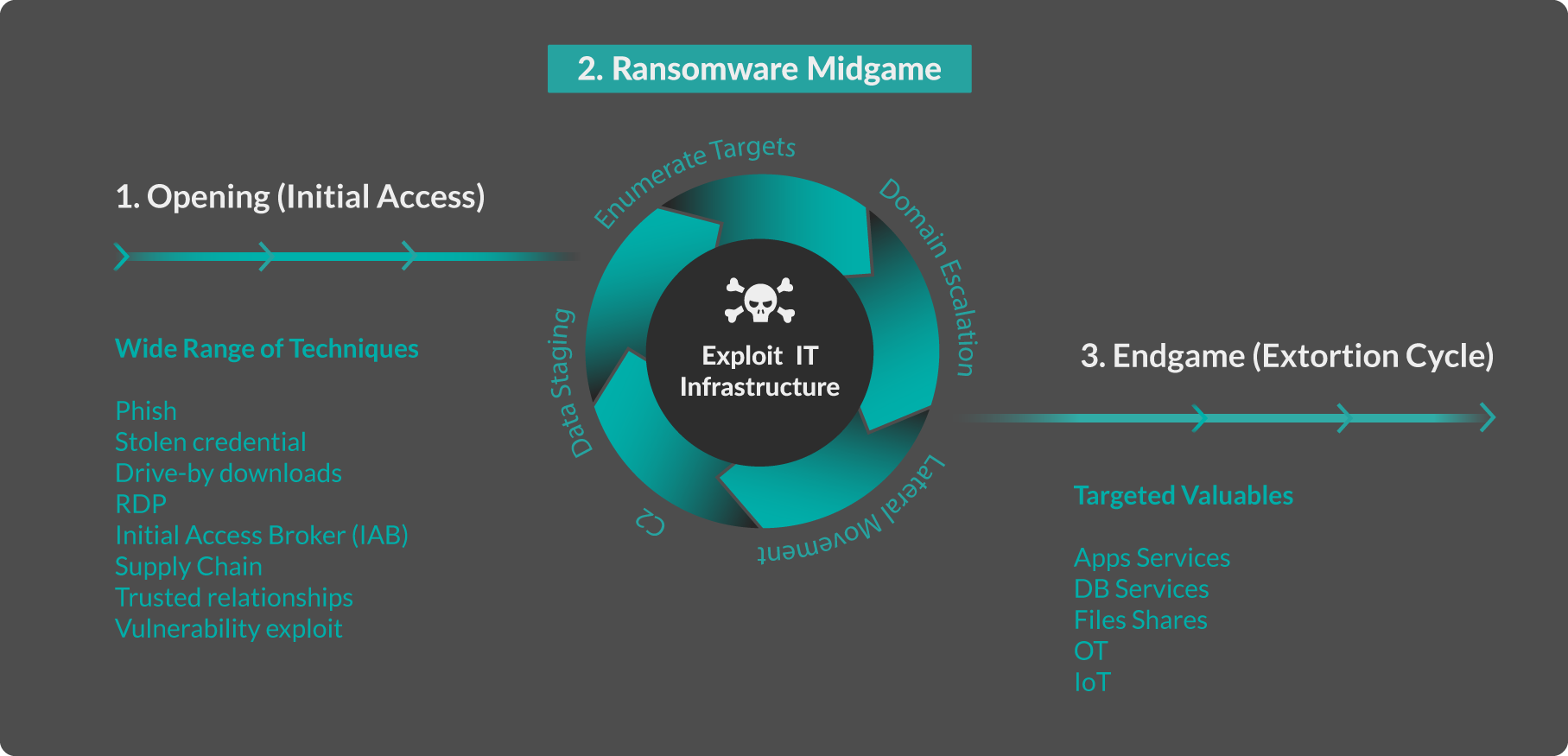
Unlike advanced persistent threats (APT), or cyberespionage, ransomware crews are less interested in the quality of what to compromise. Rather, they are more interested in the quantity or impactfulness of that compromise. Ransomware intruders are also in a rush, having an average of just five days of dwell time, to noisily accomplish their play before raising their extortion note victory flag. These motivational drivers lead to certain behaviors.
From an attacker's perspective, the inside of the network looks like a wide-open field to maraud about or a gauntlet of tripwires if it is being observed, creating an intruder's dilemma.
Five Ways Attackers Leave Ransomware Vulnerable to Detection
Interestingly, tables can turn from the attacker's to the defender's advantage in the midgame. Defenders should have a home-field advantage, know the environment, understand what is expected, and have context on users, assets, and workloads if they are watching.
The ransomware midgame is dominated by the extortion-motivated intruders' need to discover, compromise, and stage data across the network before encryption starts their endgame. These actions are modeled in five tactics and techniques repeated through each network segment until a critical mass of damage is accomplished. Each attacker's step on the network opens up another opportunity for defenders to respond before destruction is done, and the ransom note delivered.
1. Target enumeration
Target discovery and enumeration starts once an intruder lands and begins expanding their footprint within the environment.
Ransomware intruders land blind and need to gain environmental awareness. They start by using traditional network scanning tools, e.g., NMAP, ping, net, etc., to get the lay of the land. Next, the RaaS playbooks and post-mortem evidence show that attackers focus on Active Directory (AD) in order to maximize the damage while reducing dwell time.
Commonly used AD enumeration tools include: Nltest, AdFind, Powerview Get-ADGroupMember, MSRPC, OSINT, and BloodHound.
2. Domain escalation
Ransomware attackers establish a beachhead on any easily accessible host. However, they may not have the privileges needed to accomplish their goals from that position. To gain access, intruders exploit directory hierarchy vulnerabilities, decode hashed passwords left on hosts (e.g., LSASS), reuse stolen credentials, or exploit the myriad of configuration errors found on domain controllers.
With escalated privileges, intruders take control of other assets and data services in that domain or pivot toward adjacent, more lucrative segments.
The most damaging incidents include vertical privilege escalation to Domain Admin. The attacker gains the ultimate rights, even leveraging GPO to push malware as a software update in one motion, without slow hands-on keyboard hacking.
Domain escalation tools and vulnerability exploits commonly used include DCSync, Zerologon, Rubeus, Cobalt Strike, Mimikats, WMI, Ticket forgery, and PrintNightmare.
3. Lateral movement
Modern ransomware searches for volumes of assets and data to improve its payment calculus before springing its encryption trap. Intruders expand their controls beyond the beachhead by moving laterally through the victim's environment, exploiting unmonitored and assumed trusted east-west communications.
Ironically, intruders regularly reuse living-of-the-land tooling made available by IT operations for network-wide systems administration.
Lateral movement tools commonly used include PSExec, RPC, Powershell, WMI, and Cobalt Strike.
4. C&C
Once the intruder has mapped the environment, enumerated assets, and marked data to compromise, they call home to command and control (C&C) infrastructure to get orders and additional tooling.
Intruders apply C&C obfuscation techniques to avoid detection as they cross firewalls. The obfuscation techniques include creating tunnels over DNS and HTTP, encrypting egress communications, or using tooling like F-Secure C3.
5. Data Staging
Data is the lifeblood of businesses. Not having access to that data is the leverage extortionists hold over their victims. Along with AD, ransomware tactics prioritize compromising file systems, databases, and backup platforms as the fast path to strengthen their payment calculus.
The ransomware midgame's land-and-pivot workflow exploits trusted relationships between users and applications' access to data inside the perimeter. As a result, the assumptions made in data access management breakdown give intruders the ability to misuse data systems for staging data before exfiltration and encryption starts.
Additionally, data storage systems share a prevalence of unpatched vulnerabilities, weak security controls for performance tradeoffs, and the prevalence of misconfigurations, similar to AD.
Data staging tools and data system vulnerability exploits commonly used include SQLi, NoSQLi, buffer overflow, Rclone, SMBclient, and Dropbox.
Take Action, Stop Ransomware Tactics in Its Midgame
Modern ransomware is an existential threat to your business. Every security leader has to answer how they are building resilience against it. The damage from ransomware is growing, which is why following the tried and failed conventional wisdom of bookending ransomware defense, focusing on initial access, and then falling back to recovery isn't enough.
The midgame is where modern ransomware does its damage and also where defenders hold an observable advantage if they are ready to fight on the inside.
Discover more