Catch Intruders in Real Time
Once an attacker breaches your perimeter defenses, the race begins. Will they find your crown jewels? Or will you detect and block them first? Your Microsoft Active Directory (AD) is a popular first stop for intruder reconnaissance, but it's also one of the busiest - and loudest - systems in your enterprise. How can you possibly identify tell-tale threat signals in all that noise?
ExtraHop Reveal(x) keeps you ahead of attackers with a comprehensive view of your AD forest and advanced machine learning to strip away the noise and automatically surface anomalies in real time so you can identify and block intruders early in the kill chain.
Complete Visibility
From rogue PowerShell scans to unauthorized privilege escalation to excessive failed login attempts, comprehensive visibility and machine-driven anomaly detection help you spot and correlate intrusive behaviours the moment they occur.
Real-Time Detection
Reveal(x) displays AD traffic flows in real time using Live Activity Maps with detection markers for any suspicious behavior. Customizeable dashboards enable you to quickly identify credentials in clear text, expired passwords, account change propogation across the environment, and much more.
Intelligent Response
Trigger real-time alerts on bad password attempts, account lockouts, administrator logins, and any other metric you care about. Reveal(x) extracts granular details from the payload for forensics and easily integrates with SIEM and incident response tools so you can find answers and act just as quickly.

What I like about this is that our security guys have, at most, two windows they need to look at. One tells them what's going on, the other tells them what has gone down and how to fix it.
Mike Sheward
Senior Director of Information Security,
Accolade
Cut Through the Noise in Your Active Directory
- Identify Intruders Early: Detect intrusive behaviors early and drill down to details in just a few clicks so your team can shut down attackers before they reach their target.
- Avoid Secondary Attacks: Proactively detecting and stopping reconnaissance means a second attack is unlikely, giving you value and peace of mind long after the first attack.
- Harden Your Defenses: Recreate the exact steps intruders took to advance an attack once inside your environment and use that knowledge to proactively strengthen your defenses.
Ready to Learn How It Works?
Meet ExtraHop Reveal(x)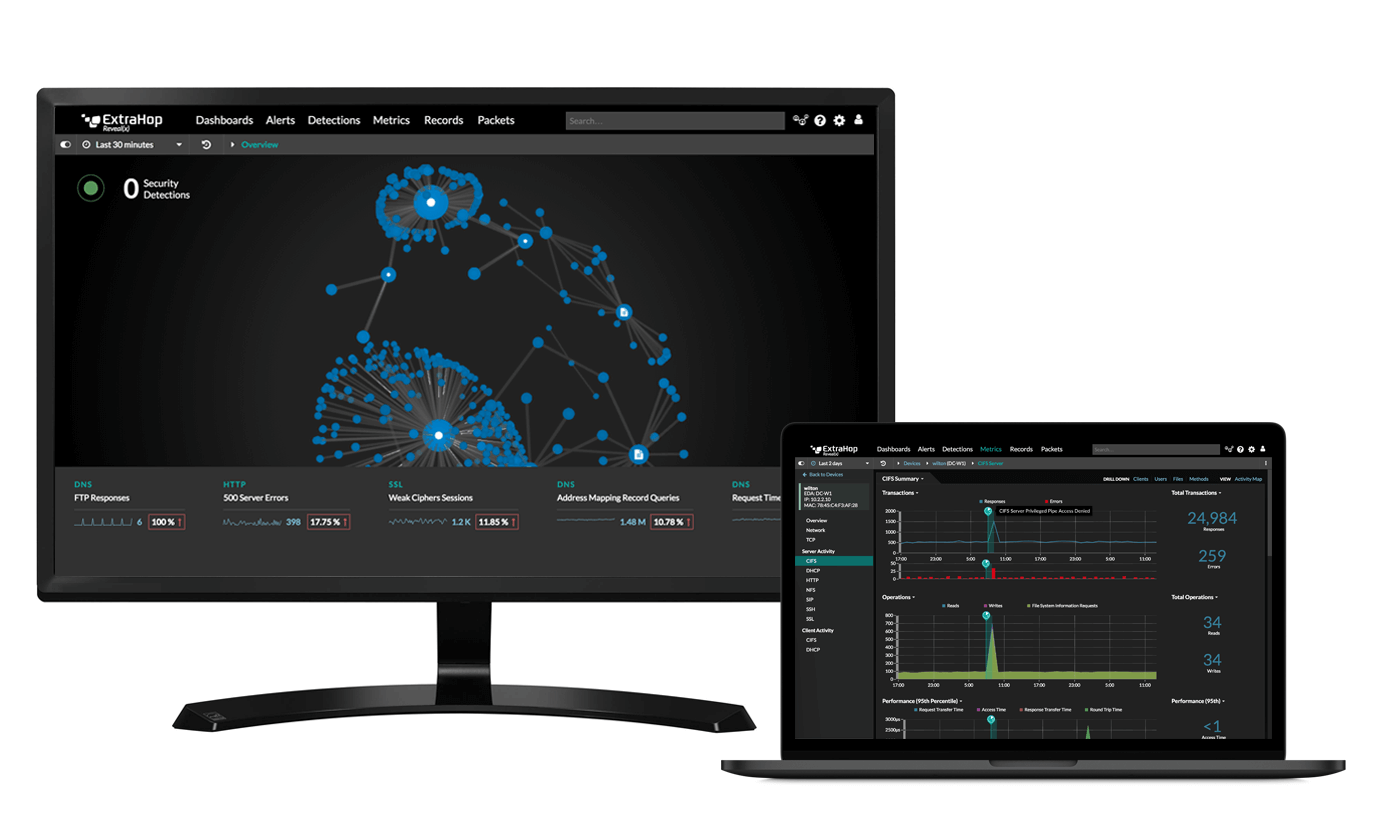
Start the Demo
Stop data exfiltration, insider threats, and more with the full product demo.
Start Demo
